Introduction
While Information Technology (IT) adoption has been widely discussed in previous studies, understanding why users adopt or refuse to adopt IT is still a research challenge. Although research about IT adoption began in the 1980s, its most notable achievements are related to identifying the factors that explain why individuals are persuaded to use IT (acceptance). In this vein, the proposed models are highly accurate in predicting acceptance (above 70% according to Venkatesh et al. (2003)). However, something that those models only explain weakly is why and how users move from the acceptance to the adoption of the new IT (Benbasat and Barki, 2007, Turner et al., 2010, Williams et al., 2009).
In this sense, a neglected research topic is how IT adoption occurs within work team environments. In fact, this issue raises doubts about the applicability of the ongoing models in real-life settings. For example, we do not fully understand how the adoption of sophisticated technologies occurs within small groups (Venkatesh et al., 2003). In particular, to our knowledge, no empirical research has addressed the question of how users elaborate their speech during an IT adoption process, in spite of the fact that Diffusion of Innovations Theory (DOI) claims any innovation – including IT innovations – is a process of communication (Rogers, 2003). Therefore, analyzing how users communicate and elaborate their discourse might be a relevant topic to understand the IT adoption process, but this subject has not been researched previously.
To address this issue, we studied the adoption of an online quiz system among a group of three first-year engineering lecturers. Specifically, we analyzed their speeches during a training session on the software. Discourse analysis was used methodologically to understand and classify the rhetoric of attendees to the training session. The discourse analysis method is a novel and interesting approach to the analysis of the participants’ acts of communication within their contexts and through their speeches. Some well-known psychological theories have been built by the use of qualitative methods, such as Grief Model (Kübler-Ross, 2009).
The remainder of this paper has four sections. The second section summarizes previous works; the third section describes the method used in this study, the fourth section synthesizes the main results, and the last section contains a summary and a conclusion.
Related works
Research on IT adoption has been dominated to a large degree by the use of causal-statistical models. In particular, much of the literature deals with individual-based models (the most known of them: Technology Acceptance Model, TAM). In 1989, Davis presented TAM to answer the question why users do use technologies (Davis, 1989, Davis et al., 1989). Later, other researchers extended TAM to a second improved version referred as TAM2 (Venkatesh and Davis, 2000). While the latest one (TAM3) was developed by Venkatesh and Bala (2008).
TAM represents a seminal work into the research on the individual acceptance of technologies (Wu, 2012). In fact, TAM has been so important for IT adoption research that almost all later models refer to the Davis’ work. For example, Venkatesh et al. (2003) published their Unified theory of acceptance and use of technology (UTAUT), which is based on TAM and other seven models. After this work, a greater number of researchers have been making progress in either extending TAM or validating it. In this sense, one of the latest models proposed is UTAUT2 (Venkatesh et al., 2012). Other works that follow this individual-causal line are the Task-Technology Fit Model (Goodhue and Thompson, 1995) and Delone and McLean (2003).
From a critical point of view, although IT adoption has been widely studied, an important limitation of most previous works lies in the fact that they have analyzed this phenomenon from an individualistic perspective. This limits the application of these models to real social contexts. In fact, it is a remaining issue to test the applicability of models such as TAM in real settings. For example, IT adoption in work team environments is not well understood yet (Venkatesh et al., 2003). In other words, the fact that research on IT adoption is dominated by traditional paradigms might constrain a complete understanding of this phenomenon. IT adoption should not be limited to a set of predictive factors, assuming these variables are in a static domain, but IT adoption has to be seen as a dynamic process that evolves over time as well. However, mainstream models do not include this perspective (Delone and McLean, 2003).
The bias in the literature to build variance models has triggered a debate into the international scientific community (Mora, 2013, Williams et al., 2009). Currently, most renowned scholars converge in calling for a change in the perspective to understand IT adoption (Dwivedi et al., 2015). These researchers have started to suggest two nonexclusive new strategies to deal with these challenges. Firstly, they propose to change the current mainstream (positivist and quantitative) and to introduce contributions from alternative research methods (Benbasat and Barki, 2007, Dwivedi et al., 2015, Walsham, 2012, Williams et al., 2009, Wu, 2012). Secondly, they also suggest focusing on the IT adoption process as a whole (Schwarz et al., 2014). For example, Michael Myers on Dwivedi et al. (2015) claims “The conventional wisdom might be necessary, but it is not sufficient. Maybe it is time to re-think IT implementation”.
Regarding the IT adoption process, to our knowledge, there is no research on the collective discourse elaborated by users when they are adopting a new IT. However, this issue might be highly relevant because IT adoption, as innovation phenomenon, is a process of communication (Rogers, 2003). Therefore, how users communicate with each other and transmit their perceptions and fears about the implementation of a new IT might be critical for the success or failure of an IT project.
There is some evidence showing the important role played by the mutual influence of users during the processes of adoption. For example, the well-known model, UTAUT, includes social influence as a predictor of expected performance (Venkatesh et al., 2003). Also, research using a process approach has found users modify their attitude toward the IT during the implementation. Indeed, Schwarz et al. (2014) found several users changed their initial reluctant attitude toward a new Enterprise Resource Planning. According to these authors, users move through different stages during the IT adoption process. In some stages they gather information, and in others, they make decisions whether accepting or rejecting the new IT. As a result, users can keep or change their decisions on whether adopting or not a new IT. This decision depends on the mutual interaction among group members. They concluded “An end user will look to fellow co-workers for support and for cues as to how to react to the introduction of the new technology. Users form a social group and exchange information about the new IT; it is these groups that are critical to individual responses to new technology”.
DOI gives theoretical support to this research. According to DOI, the outcome of an innovation process might not necessarily end up at the acceptance stage, because the new IT might be rejected at more advanced stages (Rogers, 2003). Indeed, Rogers claims that members of the group receive greater amounts of information about the innovation, as they progress among adoption stages. These increasing volumes of information come from two sources: the knowledge acquired by individuals when using the new IT, and the information shared by group members about the adoption process. The first source includes new knowledge about characteristics of the innovation as relative advantage, compatibility, and complexity; while the second source includes observability of the innovation and social influence.
Summarizing, even though research on IT adoption has achieved a remarkable development, there is still room to grow. Researchers have put a considerable effort in knowing the factors conditioning IT acceptance. However, most works tend to use quantitative approaches in obtaining static causal relationships among factors. In this sense, a less known topic is about understanding how new IT users mutually interchange their views, and show their fears concerning that new IT. Understanding this issue might be a relevant matter because, as it was mentioned, any IT adoption is a social phenomenon as well. Users’ interactions might influence their attitudes toward routinization, either fostering or constraining them. Therefore, the research question of this paper is:
RQ: Are there differences between the discourse of the users who succeeded or failed in a new IT adoption?
Method
This section is divided in two subsections. The first subsection describes the process of data collection. The second subsection presents the methodological analysis.
Participants
Data were collected during the implementation of a system of quizzes based on Moodle among a group of lecturers of a Chilean university. They hoped the system would enable them to take short-examinations to improve the students’ performance but without increasing their workload. As a part of the project, participants had to take part in a training session on the software (Moodle). In order to collect qualitative data, the session was videotaped and dialogs were transcribed.
Lecturers taught in first-year engineering courses. They participated in the project either voluntarily (volunteer) or compelled (compel). Moreover, not everyone finally adopted the system. Table 1 shows a description of each participant in the training session and the corresponding outcomes of the adoption at the end of the project.
Data Analysis
Discourse analysis method: Antecedents.
Discourse analysis procedure was used to examine the information. Discourse Analysis is a discipline that has evolved from different theoretical pathways. From a scientific perspective, two mainstreams can be distinguished. The first one understands discourse as an object of study, while the second one uses discourse as a method to analyze data (Ludovic et al., 2006). In this research, discourse is understood as a method to analyzing data through an interpretative approach. In this context, an organization is seen as a subjective world, and discourse analysis is interested in the mental representations of the actors within that subjective world (Giroux and Marroquin, 2005). In that sense, our aim is not to classify structures of speech, but rather to deconstruct the socio-psychological features behind the content of what people tell to others, i.e., to discover the underlying meanings of the speech (Giroux and Marroquin, 2005).
Language wrings different types of meanings: propositional, social, emotional, and so on. Austin (1962) was a pioneer in pointing out that any individual speaking can make different actions through his/her words. He proposed that into a communication process, sentences and questions have to be seen more than just statements, but rather as actions: “to tell is to do.” In other works, the oral discourse has been seen as polyphony. That is, oral discourse is not just interesting for the content itself, but also by its expected impact on the social construction of reality (Berger and Luckmann, 1966). Accordingly, individuals and groups construe the reality and, at the same time, that new reality is structurally coupled to the individuals’ cognitive structure and their value systems (Riviere, 2006).
Discourse Analysis Procedure
An independent researcher conducted the discourse analysis. She did not attend the training session and worked with the transcriptions. In order to validate her analysis, the independent researcher exposed findings to Re in several meetings after the project had finished. Such as it is described at Table 1, Re had been involved in the entire project, including the training session.
The analysis process is described below. Firstly, participants were divided according to their outcomes: whether they eventually adopted the system or not. Secondly, each participant’s statements were analyzed according to the previous classification. Thirdly, a transverse discourse analysis was performed to examine the statements; this procedure is based on lexical identification (Alvear, 2011, Alvear and Tello, 2014). Through this procedure, three categories were extracted: social and discursive context, communication analysis, and communication function.
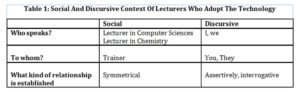
Category “social and discursive context,” considers the contextual aspects of the discourse. These aspects include those elements needed to understand properly the meanings of the statements and are different from the semantic itself (Charaudeau and Maingueneau, 2002). Such context is analyzed from a social and discursive perspective through three questions: Who speaks and to whom is addressing her discourse? and What kind of relationship is established? (i.e. operational questions).
Table 1: Attendees to the training session and their corresponding outcomes

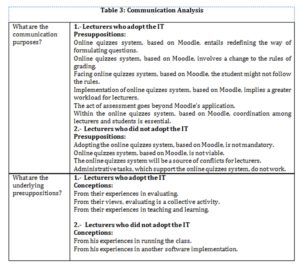
Category “communication analysis” is aimed to identify the speech’s argumentative structure, which includes both cognitive and discursive perspectives. This content is obtained by two operational questions: What are the communication purposes?, and What are the underlying presuppositions? The former tries to establish the interpretative framework while the latter tries to identify the underlying conception of reality supporting the communication process.
Finally, the category “communication function” is aimed to identify the roles played by participants in the communication process. In this case, the roles played by the attendees during the training session.
Results and Discussion
This section is divided in two subsections. The first subsection describes the process of data collection. The second subsection presents the methodological analysis.
Results are grouped into three methodological categories: social and discursive context, communication analysis, and communication function. Each of these categories is presented below.
Social and discursive context of communication activity
Who speaks and to whom is addressing her discourse?
Semiolinguistic theory of language understands the act of language as an acting that confronts two spaces of meaning (Charaudeau, 1984). Firstly, “on deeds” (situational) or external represents the space occupied by the act of a compromised language. The second, “on words” (discourse) or internal, that is defined as the place where the discursive instance occurs (Charaudeau, 1984). Both spaces will be presented below.
From a situational or external perspective, just in this moment, the opposed duality, speaker/interlocutor, appears represented by the relationship lecturer/trainer. They speak from their social role in the project; namely, they do not speak as isolated individuals, but as individuals who have a particular role in the organization. Consequently, everyone speaks on behalf of his/her own position. That is, as a Lecturer in programming (CS), or a Lecturer in Chemistry (Ch), or a Lecturer in Physics (Ph) and as the Trainer (Tr) (see Appendix, Table 1 and 2). In this sense, communication activities are based on participants’ social identities. For example, in the first three cases, the speaker is a lecturer, as it can be inferred from Statement 1.
Statement 1: For example, what if the student scores three? [Note: The lowest score in the Chilean Educational Scale is one. The maximum is seven; being four the minimum to pass] And, I assume that scoring four or five means the student has learnt what she needs. How this can be configured [in Moodle]?
From a discursively perspective, the opposed dyad <addresser/addressee> is expressed by pronouns. <I, we, neutral/you, they, you all>. Lecturers who eventually adopted the new IT system (Ch, and Cs) utilized the discursive relationship based on <I, we/you, you all>. That reveals that addressers express themselves in first person, either singular “I” or collective “We.” According to Ducrot (1984), these types of findings show addresser expresses herself by a more subjective, honest, and intimate style of communication. As it can be extracted from Statement 2 (see Appendix, Table 1):
Statement 2: … but this problem is out of this project hands. I believe, it is such an important and complex matter that requires to be dealt with as a Department.
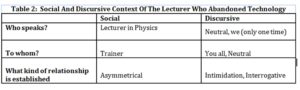
In contrast, the lecturer who abandoned the system established a discursive relationship based on <neutral/neutral, you all>. Therefore, the addresser adopts a more objective position, detached, without committing, and keeping a distance from his addressee (Ducrot, 1984). As it can be extracted from Statement 3 (see Appendix, Table 2).
Statement 2: There are many students who cannot take the course. They want to do it, but [they cannot do it because] they are in debt either with the University or with the Library. A number of [special] cases [will pop up] that will affect the functioning [and operability of the system]. Thus, who will have to solve the problem at the classroom? [I guess] the lecturer.
What Kind Of Relationship Is Established?
We observed that lecturers who adopt the system, Ch and Cs, tend to establish assertive and symmetrical power relationships (see Appendix, Table 1). Namely, addressers (i.e., the lecturers) communicate their message looking for the commitment of the addressee (i.e., the trainer) when she gives an answer to the questions. In contrast, the lecturer who abandoned the system, Ph, establishes power relationships based on intimidation using a questioning and asymmetrical style of communication. That is, he looks for confronting the addressee (see Appendix, Table 2).
Communication Analysis
What are the communication purposes?
Lecturers’ communication activities were based on their previous communicational experiences, either oral or written, and the relationships they have established with other spaces of activity as educators (see Appendix, Table 3). Namely, both previous experiences and other ongoing conditions, at the moment of the training session, shaped their behavior. For example, Statement 4 shows that Ch’s communication is based on the ongoing activities and those she will be doing in the future (she is concerned about who will be uploading the questions, after the implementation finishes) . We inferred that she acts assuming her social role as a lecturer, but she is also doing an assumption: this system will mean a greater workload.
Statement 4. Here, the aim is that every lecturer does the same as you [Note: talking to Trainer]. I mean, in the project it is written what has to be done? The idea is, for example, that [lecturers in] Chemistry would upload their questions (…) but, in this sense, who will [really] be uploading those questions? (Trainer: I did it…) Ah! That’s I’m telling you. That’s the idea. So, you did upload the questions this semester, and in the future, who will upload the other questions? (Trainer: each one will be doing it).
What are the underlying presuppositions?
Lectures make communication activities from their conceptions of the space of activities. Those spaces of activities may be both of themselves, as addressers, and of others (e.g., Trainer). Likewise, they also make it from the future views of such actions, “in the future, who will upload the other questions? (See Appendix, Table 3). For example, in Statement 4, the lecturer speaks from her professional experience. That follows educational theory, in the sense that, at a cognitive level, people communicate with each other based on their collective memories (Bruner, 1966)
Communication Function
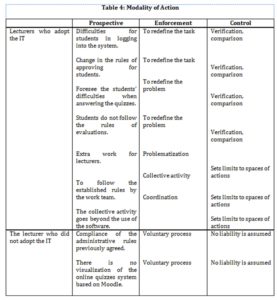
In general, when lecturers communicate, they use three modalities of action: prospective actions, enforcement actions, and control actions. Those lecturers who adopted the system (Ch and Cs) tried to foresee the future use of Moodle. In other words, they see themselves using the system. This visualization is based on both their own experience and the relationship established with other spaces of action. For example, at the first part of Statement 4, the lecturer realizes the task that she will have to do: “upload other questions to Moodle”.
Visualization facilitates an instance of problematization, i.e., a difficulty is identified, and, at the same time, possible solutions are analyzed.
Statement 6: This is what I am pointing out. I did know that [my colleague] has sent you a database with questions… [Trainer: OK]…So, who will be uploading those questions?
That interaction triggered redefining task and control actions.
Statement 7: [Yes,] I did it.
Statement 8: Ah! That’s I’m telling you. That’s the idea. So, you did upload the questions this semester, and in the future? (Trainer: Each one will have to do it).
Those statements show the roles played during the implementation and the setting of limits about both spaces of action and responsibilities. Moreover, we observed the lecturer analyzes and projects the difficulties that will be caused using the application. Thereafter, she plans the future contingent actions (problematization).
Unlike Ch and Cs, the lecturer who did not adopt the system does not display communicational activities oriented toward future contingent actions. For example, see statement 9.
Statement 9: … This [kind of] requirement is for you. Do you believe the student will go to you? [Note: confronting to Tr]. I think this is a very interesting system, but its operation seems complex.
The above is guided by previous negative experiences of that lecturer with other systems’ implementation.
Statement 10: Thus, what will happen is this: Students will say in class: ´prof, yesterday I tried to log into the system, but I couldn’t do it´. What will be the procedure to add that student asap? (Tr: Eh [Note: She takes time to answer])… Do you know why I am asking this? I worked with Moodle before and had that problem.
Therefore, Ph undermines the project using his negative experiences as an argument. Also, he wants to influence other lecturers through this argument.
Answering the RQ (Are there differences between the discourse of the users who success or failed in a new IT adoption?)
In this research, we were interested in the oral communication of users, who participated in a training session. We found meaningful differences in the style of communications among users who either eventually used or not the new IT. This might shed light on understanding the success or failure of IT adoptions.
Regarding the lecturers who adopted the system, they used expressions in the first person, with commitment, and adhering to the project’s objectives. They tend to establish symmetrical and assertive power relationships with the Trainer. Moreover, their statements are emitted as a function of both their experience and their self-perception of role (e.g. as a lecturer). Thereafter, they foresee how technology could help to improve their role performance, especially by visualizing their future performance. That compels to define the type of role being played, which in turn requires control actions, such as verification and comparison.
In contrast, the lecturer who abandoned the technology used statements expressed in a neutral or passive language [There has to be done, it could be]. Namely, he is not committed to the project and keeps distance from the discourse of both other lectures and the project’s objectives. Moreover, his statements are emitted based on previous negative experiences with other IT’s implementations. For that reason, the way he conceives the system is strongly negative, a condition that makes him difficult to see a future performance.
This last one is consistent with the discursive theory. An act of language is a product of psycho-social entities that are partially aware of their community’s practices and imaginaries. Likewise, when an individual emits an act of language, she/he tries to influence others (Charaudeau and Maingueneau, 2002).
Conclusions
Finally, we conclude that there are discursive differences between users who adopt a system and users who do not adopt it. Lecturers who adopted the system used a compromised form of speech in alignment with the project objectives. In addition, they established an assertive style of communication, based on symmetrical power relationships. Furthermore, they utilized a discourse that was always grounded on their own experience and social role as educators. Furthermore, we observed they developed discursive strategies visualizing (projecting) themselves using the system in the future. These strategies had four elements: foreseeing the problem, establishing solutions, assigning responsibilities and defining action space.
On the other hand, the lecturer who did not adopt the system used a discourse separate from the project’s objectives. Additionally, he established a communication based on asymmetric and intimidating power relationships. In addition, his expressions were greatly influenced by a negative experience about a failed previous project. This negative experience prevented him from visualizing himself using the system in the future. Interestingly, he did not establish responsibilities or define an action space, i.e., he never established his duties or defined what would be the responsibilities of others involved, demonstrating early on that he really had not planned to use Moodle.
These differences among discourses would enable us to infer that contrasting discourses could help to predict whether a user is willing to use a form of technology or not. For example, a committed and assertive discourse versus a more neutral one, based on intimidation, could be a predictor of success or failure of its adoption by users.
It is worth mentioning that the adopted literature is consistent with the results presented. Authors have consistently shown that users’ commitment is an enabler of success in IT adoption, underscoring the importance of efforts to structure preparatory activities for users engaging in the process of adoption (Agarwal, 2000, Bagayogo et al., 2013).
The findings make three relevant contributions to the theory and practice. Firstly, results contribute to a better understanding of the adoption process. In particular, findings show that users express their agreement or refusal to adopt a new system through discourses. Therefore, a project leader may identify which users are more committed to using a new form of IT. Secondly, discourse analysis is a novel, methodological lens that brings innovation to the way that IT adoption has been studied. In that sense, this research is in line with the wishes of researchers to seek new methodological perspectives to better understand why users adopt or reject a new system (Dwivedi et al., 2015, Wu, 2012). Thirdly, results may help practitioners to understand the relevance of what the users are communicating and how they are doing so. In this sense, discursive analysis provides a tool which can anticipate user resistance.
This research has two major limitations that invite further studies on the subject. Firstly, the study was done with a very special and small sample of users who are highly-qualified professionals (lecturers), representing a very biased population of users. The sample size makes it difficult to generalize the results. Secondly, data were collected at just one moment during the entire process. Therefore, future works should extend findings to other users, organizational contexts, and the whole process. Finally, we encourage other researchers to analyze what users communicate during the adoption of forms of IT.
(adsbygoogle = window.adsbygoogle || []).push({});
References
- Agarwal, R. 2000. Individual Acceptance Of Information Technologies. Framing The Domains Of It Management: Projecting The Future Through The Past. Cincinnati, Oh: Pinnaflex Press.
- Alvear, S. 2011. Fonction Sociale Des Activités De Qualification. In: Barbier, J.-M., Chauvigné, C. & Vitali, M.-L. (Eds.) Diriger: Un Travail. Paris: Editions L’harmattan.
- Alvear, S. & Tello, J. 2014. El Discurso Directivo En La Comunicación De Los Estados Financieros El Caso De Dos Empresas Chilenas. Contaduría Y Administración, 59, 261-283.
Google Scholar
- Austin, J. 1962. How To Do Things With Words, Uk, Clarendon Press, Oxford.
- go, F., Beaudry, A. & Lapointe, L. Impacts Of It Acceptance And Resistance Behaviors: A Novel Framework. In: Pennarola, F. & Becker, J., Eds. International Conference On Information Systems (Icis 2013), December 15-18 2013 Milano, Italy. Bocconi University.
Google Scholar
- Benbasat, I. & Barki, H. 2007. Quo Vadis Tam? Journal Of The Association For Information Systems, 8, 211 – 218.
Google Scholar
- Berger, P. & Luckmann, T. 1966. The Social Construction Of Knowledge: A Treatise In The Sociology Of Knowledge, Garden City, Ny, Anchor Books.
- Bruner, J. 1966. Toward A Theory Of Instruction, Cambridge, Mass, Harvard University Press.
Charaudeau, P. 1984. Une Théorie Des Sujets Du Langage. Langage Et Société, 28, 37-51.
Google Scholar
- Charaudeau, P. & Maingueneau, D. 2002. Dictionnaire D’analyse Du Discours, Paris, Seuil.
- Davis, F. 1989. Perceived Usefulness, Perceived Ease Of Use, And User Acceptance Of Information Technology. Mis Quarterly, 13, 319-340.
Google Scholar
- Davis, F., Bagozzi, R. & Warshaw, P. 1989. User Acceptance Of Computer Technology: A Comparison Of Two Theoretical Models. Management Science, 35, 982-1003.
Google Scholar
- Delone, W. & Mclean, E. 2003. Information Systems Success Revisited. Journal Of Management Information Systems, 19, 9 – 30.
Google Scholar
- Ducrot, O. 1984. Le Dire Et Le Dit, Paris, Éditions De Minuit.
- Dwivedi, Y., Wastell, D., Laumer, S., Henriksen, H., Myers, M., Bunker, D., Elbanna, A., Ravishankar, M. & Srivastava, S. 2015. Research On Information Systems Failures And Successes: Status Update And Future Directions. Information Systems Frontiers, 1-15.
Google Scholar
- Giroux, N. & Marroquin, L. 2005. L’approche Narrative Des Organisations. Revue Française De Gestion, 159, 15-42.
Google Scholar
- Goodhue, D. & Thompson, R. 1995. Task-Technology Fit And Individual Performance. Mis Quarterly, 19, 213-236.
Google Scholar
- Kübler-Ross, E. 2009. On Death And Dying: What The Dying Have To Teach Doctors, Nurses, Clergy And Their Own Families, Taylor & Francis.
Google Scholar
- Ludovic, C., Frédérique, D. & Saboly, M. 2006. Éditorial – Discours(S). Entreprises Et Histoire, 42, 5-6.
- Mora, M. 2013. [Aisworld] A Small Revolution In The Is Field [Online]. [Accessed May 01 2013].
- Riviere, A. 2006. Le Discours Organisationnel Vu Par Les Sciences De Gestion: Monologue, Polyphonie Ou Cacophonie? Entreprises Et Histoire, 42, 29-45.
Google Scholar
- Rogers, E. 2003. Diffusion Of Innovations, New York, Free Press.
- Schwarz, A., Chin, W., Hirschheim, R. & Schwarz, C. 2014. Toward A Process-Based View Of Information Technology Acceptance. Journal Of Information Technology, 29, 73-96.
Google Scholar
- Turner, M., Kitchenham, B., Brereton, P., Charters, S. & Budgen, D. 2010. Does The Technology Acceptance Model Predict Actual Use? A Systematic Literature Review. Information And Software Technology, 52, 463-479.
Google Scholar
- Venkatesh, V. & Bala, H. 2008. Technology Acceptance Model 3 And A Research Agenda On Interventions. Decision Sciences, 39, 273-315.
Google Scholar
- Venkatesh, V. & Davis, F. 2000. A Theoretical Extension Of The Technology Acceptance Model: Four Longitudinal Field Studies. Management Science, 46, 186-204.
Google Scholar
- Venkatesh, V., Morris, M., Davis, G. & Davis, F. 2003. User Acceptance Of Information Technology: Toward A Unified View. Mis Quarterly, 27, 425-478.
Google Scholar
- Venkatesh, V., Thong, J. & Xu, X. 2012. Consumer Acceptance And Use Of Information Technology: Extending The Unified Theory Of Acceptance And Use Of Technology. Mis Quarterly, 36, 157-178.
Google Scholar
- Walsham, G. 2012. Are We Making A Better World With Icts&Quest; Reflections On A Future Agenda For The Is Field. Journal Of Information Technology, 27, 87-93.
- Williams, M., Dwivedi, Y., Lal, B. & Schwarz, A. 2009. Contemporary Trends And Issues In It Adoption And Diffusion Research. Journal Of Information Technology, 24, 1-10.
- Wu, P. F. 2012. A Mixed Methods Approach To Technology Acceptance Research. Journal Of The Association For Information Systems, 13, 172 – 187.
Appendix: Analysis Tables