Introduction
This new-millennium crime, popularly known as identity theft, has been causing a lot of concern globally (Hoar, 2001; Squared, 2005; Privacy Rights Clearinghouse, 2007; IACP National Law Enforcement Policy Center, 2002). According to Finklea (2010), statistics involving identity thefts have increased over the past decade as many people are unaware and ignorant of the existence of this crime until the individual realized that his or her personal bank accounts have been tampered with, where in most cases, the damage has already been done (Squared, 2005; Berghel, 2000; Abdelhalim & Traore, 2007).
Regardless, the term ‘identity theft’ is neither consistently defined nor consistently used to describe criminal acts where the perpetrator fraudulently obtains and uses another person‘s identity (Gercke, 2007). Identity theft can simply be defined as the theft or assuming another person’s identity with the real individual’s knowledge, that is, an act when a person steals another’s identity without permission with the intention to commit fraud or other crimes (Gercke, 2007; The New York Times, 2011; IACP National Law Enforcement Policy Center, 2002; Elbirt, 2005; Pastrikos, 2004; Perl, 2003, Saunders & Zucker, 1999).
Identity theft is made possible with the help of digital information technologies (Caeton, 2007) and by the nature of modern payment systems. For example in e-commerce, sellers are willing to offer goods and services to strangers in exchange for a promise to pay, provided the promise is backed up by data that link the buyer to a specific account or credit history (Anderson et al, 2008). Identity theft involves acquiring enough data about another person to counterfeit this link, enabling the thief to acquire goods while attributing the charge to another person’s account (Anderson et al, 2008). Furthermore, identity theft is the taking of a victim’s identity to obtain credit or credit cards from banks and retailers, steal money from the victim’s existing accounts, apply for loans, establish accounts with utility companies, rent an apartment, file bankruptcy, or obtain a job using the victim’s name (identity theft, 2010). In short, identity theft occurs when someone appropriates your personal information without your knowledge to establish a parallel identity.
In 2004, 9.3 million Americans — or one in every 23 adults — were victims of identity theft. The dollar cost impact is gargantuan. Identity theft crimes tallied $52.6 billion in costs in 2004. This amounts to almost $200 for every man, woman, and child in the U.S. In five years, federal officials say people will be more likely to be a victim of this crime (Squared, 2005). Consequently, the study comes at an opportune time as citizens need to be alert and be more careful with their personal documents. In fact, the movie, “The Net” starring Sandra Bullock is a perfect example of what cyber terrorists are capable of and victims of identity thefts will have a difficult time proving who they are without proper documents.
Statistics for identity theft is on the increase annually. In 2008, identity theft affected 10 million victims most of them did not have the chance to get help to recover from their losses nor given protection by their home country (Tom, 2009). In Malaysia, the citizen’s identity card known as MyKad has an embedded microchip that contains the individual’s personal information including access to bank accounts. Previously, it was easy for Malaysians to acquire the MyKad from the National Registration Department; however, with reported losses of cards amounting to 2,123,611 the past seven years, the Parliamentary Secretary of the Home Affairs Ministry, Datuk Abdul Rahman Ibrahim announced that fines will be imposed to compel people to be more responsible with their MyKad. “This year, 58,839 people lost their MyKad, which means about 1,000 people lose their cards daily. These people gave various reasons for losing their cards, like misplacing and carelessness” (The Star, 2011).
With the influx of illegal immigrants to Malaysia, the need to acquire proper documents is imminent to these foreigners to avoid being caught and deported. Consequently, the MyKad and the Malaysian passports are indiscriminately sold in the black market. What the aliens did not know is that the MyKad is actually secure and reliable with less invasion of privacy, forgery and identity theft (Loo et al, 2009). Immigration and law enforcement officers are trained to detect fake cards immediately. However, some isolated cases have surfaced where stolen cards have been misused by offenders to commit financial fraud, applications of car and housing loans, credit card and internet banking transactions, mobile phone bills, property deals and company registration. Some of these transactions are routine activities for Malaysians yet the risk of being an identity theft victim is possible (New Straits Times, 2006). For instance, it was reported by the media that an illegal immigrant, using a stolen MyKad was able to get a job as a security guard at one of the country’s biggest security companies. He was able to enjoy the same benefits of a true citizen but the possibility of harming the company and country is probable (New Straits Times, 2006). On the other hand, victims of identity thefts were unable to get help as they are unable to provide the necessary evidence to prove their innocence. In fact, the victim himself was unaware that his personal information have been stolen and used by the offenders to commit fraudulent activities. This is unfair to the victim because the law itself such as criminal law does not recognize the person as the identity theft victims (Copes & Vieraitis, 2009). Thus, the objectives of this study were to assess the awareness of identity theft among city dwellers in the capital cities of Johor Bahru, Johor and Petaling Jaya, Selangor as well as to determine the factors to prevent identity theft.
Problem Statement
The study on identity theft is one of the most important research areas that need to be done since the level of identity theft crime is on the increase (Allison et al, 2005; Copes & Vieraitis, 2009). Stealing personal documents or hacking into the individual’s computer to obtain relevant personal information such as credit card number, bank account number, social security number, driver’s license number and other critical information (Robert, 2001) will result in a nightmare for the victim. Anyone is potentially susceptible to identity theft and safe-guarding one’s personal information is the best way to avoid being a victim. However, to curb this crime requires individuals to be aware of the existence of the crime and how it is committed. Also, citizens should be able to identify safety measures employed by them to ensure that their personal information and documents are secure.
Scope of the Study
This is a basic research focusing on residents living in the capital cities of Johor Bharu, Johor and Petaling Jaya, Selangor. Therefore, the units of analysis are the city dwellers. The choice of these two locations was determined for convenient data collection by the two researchers as these cities are their respective hometowns.
Significance of the Study
There are several valuable benefits to be learned from the outcome of this study. Firstly, the awareness among individuals on identity theft will lead to lesser occurrences of cyber crime as people will then be more careful with their personal details and not divulge them indiscriminately. Also, through the publication of the research findings in conference proceedings and journals, the seriousness of this issue will alert Malaysians to be more careful with their personal documents such as their MyKad, student cards, international passports, etc. The society will know the grim reality of identity theft and how the problem arises (Yulia, 2008). Most times, the public’s complaints are directed to the media but without any strong evidence to look into, the issue simply dissipates as the public don’t know where exactly to go to report this problem. By disseminating this information, the public will comprehend the issue and take the necessary steps to avoid being a victim.
Next, the government, relevant public agencies and policy makers will also benefit from this study. The government will have similar information for security responsibilities to agencies in their capacity as database owners, and their responsibility to the citizens in the expanding collection of activities described as “e-government” (Arnaud et al, 2000). The government will know how to create awareness of the seriousness of the consequences of identity theft and of the countermeasures which individuals and companies can take; ensuring that individuals have effective means for reporting identity theft and mitigating its consequences (Copes and Vieraitis, 2009; Arowosaiye, 2008).
Literature Review
Identity theft involves criminals stealing the personal details of others, which can then be used by the thief for personal gain (Copes, Kerly & Kane, 2010). There are only two basic types of actual identity theft. The first of these is generally the easiest and most basic way for thieves to achieve their objective (Rafla, 2005). This works out extremely well for the thief, as the credit card owner doesn’t usually notice the additional purchases until they either receive their monthly statement in the mail or have attempted to use the card and found that it has reached the maximum limit allowed. The second type of identity theft is called application fraud, or what is otherwise known as “true name fraud”. In order for a thief to be successful at application fraud, they must have access to a good deal of your personal information such as your Social Security Number, full name, address, place of work, salary, driver’s license number and date of birth. Of course not all of these pieces of information would be necessary for a thief to get away with application fraud but certainly a combination of some of the above would be required (Rafla, 2005).
From literature reviewed, the seriousness of identity theft in developed nations should be of great concern to Malaysia. This is important in order to know the level of awareness on identity theft among Malaysians. The Unisys Security Index Malaysia had conducted a survey on the level of Personal Security concern among Malaysians in 2008. It shows that 74% of Malaysians or an estimated 8.3 million people are very concerned about unauthorized access or misuse of their personal information. It can be deduced that Malaysians are concerned about the misuse of their personal information or identity theft.
Depending on the definition of identity theft, the most common type is credit card fraud of various kinds. Evidence indicates that the extent of credit card fraud on the Internet (and by telephone) has increased because of the opportunities provided by the Internet environment (Rafla, 2005). In America, identity theft crimes in 2004 cost the country $52.6 billion in losses (Squared, 2005). This equates to about $200 for every man, woman, and child in the U.S., therefore, federal officials predicted that in five years, people will more likely be victims of this crime (Squared, 2005). Further, Grassley (2001) pointed out that the FBI estimated that 350,000 cases of identity theft will occur each year, making this the fastest growing crime in the new economy. This “white-collar” crime is stimulated as people increasingly depend on credit cards for electronic commerce and other daily business transactions in cyberspace (Arowosaiye, 2008). Furthermore, Trans Union reported that the fraud line increased from 35,000 in 1992 to more than 500,000 in 1997 and this number is expected to quadruple in ten years’ time as people rely on the internet for fast and easy transactions (Copes, Kerly & Kane, 2010).
Nevertheless, identity theft is sometimes referred to as an “enabling crime” where thieves use stolen identities to commit other crimes, including credit card fraud, immigration fraud, Internet scams, and even terrorism (McCormick, 2008). Regardless of age, victims of identity theft are usually the elderly (Douglas, 2008) as they are too trustful of people around them and will give 100% commitment or responsibility to the person they trust. The elderly are usually won over by a combination of sweet talk and a pretentious personal interest. Moreover, their physical incapability usually results in the younger generation helping them to do simple tasks such as depositing money into their bank accounts (Douglas, 2008). Even close relatives are known to deceive their elderly parents or grandparents when money gets the better of them.
Identity theft can affect all aspects of a victim’s daily life and often occurs far from its victims. Identity thieves use both traditional physical methods as well as the Internet. The most common method is computer and backup theft (Francois, 2008). In addition to stealing equipment from private buildings, criminals also strike public transport, hotels, and recreation centers (François, 2008). Next, the popular method being used by the criminals is pick-pocketing or quietly stealing a purse or wallet. Purses and wallets often contain bank cards and identity documents. Pickpockets work on the street as well as in public transport and exercise rooms (François, 2008). These documents are the foundation for identity crimes.
Methodology
The research employed cross-sectional survey design in order to integrate the different components of the research project in a cohesive and coherent way as well as to structure a research project in order to address a defined set of questions (Trochim, 2006). The sampling techniques used are stratified and sampling procedures; the former is for the identification of the location and the latter for the distribution of the questionnaire to the respondents. Consequently, the units of analysis are the city dwellers in these two locations, giving the sample size of 150 respondents.
Data collection was done by administering questionnaires to the sample size. This instrument was selected as it was the most rational choice besides being a common method for data collection. The questionnaire was developed and designed according to the research objectives and the research framework. There are three parts in the questionnaire: Part 1 is on the respondent’s demographic profile such as gender, age, race, marital status, income and education. Part 2 focused on awareness of identity theft and Part 3 on the prevention factors of identity theft. Statements in Part 2 were constructed on a scale of one to five: 5= Extremely Concerned, 4= Very Concerned, 3=Somewhat Concerned, 2= Not Concerned, 1=Don’t Know. Similarly in Part 3, scales of one to five differentiated with the following responses: was different, which are 5=Strongly Agree, 4= Agree, 3=Uncertain, 2=Disagree, 1=Strongly Disagree.
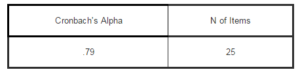
Ensuring the reliability and validity of each construct requires piloting the instrument. Reliabilty analysis allows studying the properties of measurement scales and the items that compose the scales; one of the most commonly used coefficient is Cronbach’s alpha (Sekaran & Bougie, 2010). Forty respondents were administered and the findings from the preliminary research are reported in this paper. Passing the pilot stage is a prerequisite for any research project prior to the conduct of the actual study and employing the correct statistical analysis for the data. Cronbach alpha is a model of internal consistency, based on the average inter-item correlation (Sekaran & Bougie, 2010). Table 1 shows the result of the reliability statistics which is 0.79 and this indicated high consistency and reliability of the constructs.
Table I. Reliability Analysis
Findings
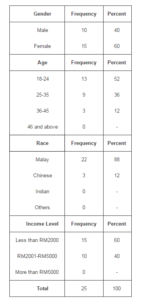
From the 40 questionnaires sent out, 62.5% completed ones were returned. As such, the results from the pilot study will be shown according to the questionnaire format. The first part of the questionnaire was on demographic profiles where the gender distribution showed that there are more female respondents (60%) compared to the opposite sex. For the age of the respondents, 52% are between 18-24 years, 36% are between 25-35 (36%) and 12% are between 35-45 years. Next, the racial distribution showed that 88% are Malays and 12% are Chinese. Lastly, for the respondent’s level of income, 60% earned less than RM2000 monthly while 40% earned an income of RM2001-RM5000 monthly.
Table II. Demographic Profiles of Respondents
Based on research question one and Table III, the mean score for awareness of identity theft is 1.6, which means that the level of awareness is low among the urban residents of both Johor Bahru, Johor and Petaling Jaya, Selangor.
Table III. Mean Score on Awareness of Identity Theft

For research question two, the factors that can prevent identity theft from occurring are shown in Table IV. The factors are also ranked according to the mean score where the first one is government policy (3.43), relevant authorities (3.39), media roles (2.94) and individual awareness (2.92).
Table IV. Factors to Prevent Identity Theft

Discussion and Conclusion
The objectives of this study were to assess the awareness of identity theft among city dwellers in Johor Bahru and Petaling Jaya as well as to determine the factors that can increase awareness of this crime. The findings from the pilot study revealed that the level of awareness on identity theft among city dwellers is low (µ =1.61) and that the highest ranked factor for the prevention of identity theft is government policy (µ =3.43). Although the findings from this preliminary investigation cannot be generalized, sufficient empirical evidence significantly shows that this white-collar crime is increasing because of the citizen’s ignorance of this problem. Nevertheless, a bigger sample size will throw more light into the situation but for now the relevant government agencies should highlight the importance of keeping our personal documents safe. With technology getting more sophisticated and the Internet becoming the main domain for e-transactions, illegal e-activities will become difficult cyber crimes to solve.
As a conclusion, city dwellers in Johor Bahru and Petaling Jaya must not remain in ignorance of such a crime. Most city folks are working people and communication should not be a problem. Reading and relaying information on cyber crimes are easier with the Internet as the tool. Besides the government and relevant authorities, the mass media should highlight the seriousness of this costly crime so that the public are better informed and the victims are able to have an avenue to turn to. Moreover, the surveyed population lived in the cities and most of them are highly educated, therefore, they should be given more information on state statutes, fraud alerts, and other relevant information by the credit reporting agencies.
References
Abdelhalim, A. & Traore, I. (2007). “The Impact of Google Hacking on Identity and Application Fraud,” Proceeding of the IEEE Pacific Rim Conference on Communications, Computers and Signal Processing, pp. 240.
Publisher – Google Scholar
Allison, S. F. H., Schuck, A. M. & Lersch, K. M. (2005). “Exploring the Crimes of Identity Theft: Prevalence, Clearance Rates, & Victim/Offender Characteristics,” Journal of Criminal Justice, 33(1), 19-29.
Publisher – Google Scholar
Anderson, K. B., Durbin, E. & Salinger, M. A. (2008). “Identity Theft,” Journal of Economic Perspectives, 22(2), 171—192.
Publisher
Arowosaiye, Y. I. (2008). “The New Phenomenon of Phishing, Credit Card Fraud, Identity Theft, Internet Piracy and Nigeria Criminal Law,” Proceeding of the 3rd Conference on Law and Technology, Kuala Lumpur, Malaysia.
Publisher
Berghel, H. (2000). “Identity Theft, Social Security Numbers, and the Web,” Communications of the ACM, 43(2), 17-21.
Publisher – Google Scholar
Caeton, D. A. (2007). “The Cultural Phenomenon of Identity Theft and the Domestication of the World Wide Web,”Bulletin of Science, Technology & Society, 27(1), 11-23.
Publisher – Google Scholar – British Library Direct
Copes, H., Kerly, K. R., Huff, R. & Kane, J. (2010). “Differentiating Identity Theft: An Exploratory Study of Victims Using a National Victimization Survey,” Journal of Criminal Justice, 9(1), 24-25.
Publisher
Copes, H. & Vieraitis, L. M. (2009). “Understanding Identity Theft: Offenders’ Accounts of their Lives and Crimes,”Criminal Justice Review, 34(3), 329-349.
Publisher – Google Scholar
Elbirt, A. J. (2005). “Who are you? How to Protect against Identity Theft,” IEEE Technology and Society Magazine, 24(2), 5.
Publisher – Google Scholar
Finklea, K. (2010). Identity Theft: Trends and Issues, Retrieved from: www.crs.gov [accessed on 2 February 2011]
Publisher – Google Scholar
Gercke, M. (2007). “Internet Related Identity Theft,” Retrieved from: www.cybercrime.com [accessed on 3 August 2010]
Publisher – Google Scholar
Higgins, G. E., Hughes, T., Ricketts, M. L. & Wolfe, S.E. (2008). “Identity Theft Complaints: Exploring State-Level Correlates,” Journal of Financial Crime, 15(3), 295-307.
Publisher – Google Scholar
Hoar, S. B. (2001). “Identity Theft: The Crime of the New Millennium,” USA Bulletin, 49. Accesses 15 February 2011 athttp://www.usdoj.gov/ciriminal/cybercrime/usamarch2001 _3.htm
Publisher – Google Scholar – British Library Direct
IACP National Law Enforcement Policy Center. (2002). Identity Theft: Concepts and Issue Paper. Retrieved 15 February 2011 at http://www.mrsc.org/ArtDocMisc/Identity%20Theft%20Paper.pdf
Publisher
Loo, W. H., Yeow, P. H. P. & Chong, S.C. (2009). “User Acceptance of Malaysian Government Multipurpose Smartcard Applications,” Government Information Quarterly, 26(2), 358-367.
Publisher – Google Scholar
Marron, D. (2008). “‘Alter Reality’: Governing the Risk of Identity Theft,” British Journal of Criminology, 48(1), 20-38.
Publisher – Google Scholar
Pastrikos, C. (2004). “Identity Theft Statutes: Which Will Protect Americans the Most?,” Albany Law Review, 67, 1137-1157.
Publisher – Google Scholar – British Library Direct
Perl, M. W. (2003). “It is not always about Money: Why the State Identity Theft Laws Fail to Adequately Address Criminal Record Identity Theft,” Journal of Criminal Law and Criminology, 94.
Publisher
Privacy Rights Clearinghouse. (2007). “Identity Theft Surveys and Studies: How Many Identity Theft Victims are there? What Is the Impact on Victims?,” Accessed 15 February 2011 at http:// www.privacyrights.org/idtheftsurveys.htm
Publisher
Rafla , A. (2005). ‘Introduction to Identity Theft,’ Journal of Social Science Research, 31(8), 28-29.
Saunders, K. M. & Zucker, B. (1999). “Counteracting Identity Fraud in the Information Age: The Identity Theft and Assumption Deterrence Act,” International Review of Law, Computers and Technology, 13(2), 183-192.
Publisher – Google Scholar – British Library Direct
Saunders, M., Lewis, P. & Thornhill, A. (2007). ‘Research Methods for Business Students,’ Great Britain, Pearson.
Google Scholar
Sekaran, M. & Bougie, R. (2010). Research Methods for Business: A Skill-Building Approach, 5th ed. USA, Wiley.
Publisher
Squared, P. (2005). ‘Identity Theft Defense Center,’ Retrieved from: www.myidcenter.com [accessed on 3 August 2010]
Shoudt, E. M. (2002). “Identity Theft: Victims ‘Cry out’ for Reform,” American University Law Review, 53(339), 340-392.
Publisher – Google Scholar – British Library Direct
The New York Times. (2011). “Identity Theft,” Accessed 15 February 2011 at http://www.nytimes.com/info/identity-theft
Publisher
The Star (2011). ‘The Fine for Losing a MyKad has been Set at RM100, a 10-fold Increase.’
Zikmund, W. G., Babin, B. J., Carr, J. C. & Griffith, M. (2010). Business Research Methods. Canada, South-Western Cengage.
Publisher – Google Scholar






