Introduction
Micro, small and medium-sized enterprises (SME) play an important role in today’s society and economy, since they represent 99 % of all enterprises in the European Union (EU). 65 million jobs depend on the entrepreneurship and innovation capabilities of these enterprises. Managing today´s complexity of IT and business simultaneously is a tremendously hard job – in particular for SMEs. Proprietors and managers of SMEs often don´t know how IT contributes to their business and occupy themselves with managing basic IT functions, which waste financial and human resources as well as limit their capacity for process and product innovation (INNOTRAIN-IT, 2011).
In a global economy speed and quality of decision-making are one of the crucial factors for success. Looking at companies like Google or Facebook it becomes clear that in the information age SMEs, especially in the digital products sector, are often not far away from growing to multinational companies within only a few years.
Based on the hyper growth-effects, as described by Shapiro and Varian, an increasing number of SME with a medium and higher share of information in their products are facing a revolution that can only be managed based on a reliable IT infrastructure. Even SMEs which are working in quite traditional areas, such as the construction or production sectors, are dependent on reliable IT systems to provide visibility into the progress of the construction side or of the production processes in their plants. Additionally, they have to fulfill an increasing number of compliance issues such as saving financial or technical data (Shapiro and Varian, 1998, Van Grembergen and De Haes, 2009,Schäfer et al., 2008).
We believe that a customized IT Service Management (ITSM) method, based on modified metamodels and frameworks can help SMEs to realize the benefits of ITSM and, as a result, gain competitive advantage and improved regulatory compliance. Hence, this paper will address the following research question:
What are the Major Steps to Design and Implement a Domain Specific Metamodel for ITSM in SME and How Should We Adapt Existing Modeling Tools?
Theoretical Background
In the early 1990’s, the “Organisation for Economic Co-operation and Development” (OECD) wrote a report about SMEs and their relation to technology and competitiveness. It was realized that IT would have a high influence on SMEs development, but the accompanying specific issues and opportunities were not clear. “Although IT enabled SMEs were identified as a driver for our economy” (Levy and Powell, 2005), research in this area remained scarce and difficult issues between IT and SME continue to persist until today (OECD, 2010, OECD, 1993). However, we believe that ITSM might provide an opportunity for SME to solve these problems, but any suggested methods and tools would have to be simple and clearly applicable, otherwise ITSM will fail to produce the improvements in SME performance that are needed for their continuing success. The following section gives a brief summary of what has been done in this area up until today and how our research will extend this body of knowledge.
IT Governance & ITSM Frameworks in Relation to SME
IT Governance and IT Service Management have inherited much from Corporate Governance and operational IT Management, but have developed into a discrete discipline with internationally recognized frameworks and standards such as Control Objectives for Information and Related Technology (COBIT), Value of IT (VAL-IT), IT Infrastructure Library (ITIL), ISO20000 and ISO38500 (Bhattacharjya and Chang, 2007, IT Governance Institute, 2003, Luftman and Kempaiah, 2007).Peterson and Van Grembergen et al.(2003) suggest that IT Governance should be implemented by a framework of structures, processes, and relational mechanisms in order to be effective.
Scientific publications about IT Governance /IT Service Management in relation to SME are very scarce and hard to find. There is little evidence to suggest that the basic IT problems that trouble SME have been resolved, which supports our contention that new approaches are needed.
Domain Specific Engineering
“Before processes and tools can be designed we must know the requirements. Before requirements can be expressed we must understand the domain” (Bjorner, 2010) this adapted version of Bjorner’s introduction to ‘Domain Engineering’ is simple, yet it reflects that basic idea behind this modeling approach. From our literature and surveys it was found that the domain of SME has special rules and requirements. Things which work effectively in a multi-national corporation need not necessarily work in a local carpenter’s shop.
We see domain specific engineering as a method, which could help to adapt existing frameworks towards meeting the needs and requirements of SMEs. Consequently, we must first establish precise descriptions of a domain; then, from these descriptions, we “derive” the domain’s requirements; and from those we can model the appropriate processes and design the tools to support entities of this domain (Bjorner, 2010).
Considerations of domains in software development have always been there. Jackson already wrote about domain specific development in 1975. His view has been followed by several other researchers and papers which have built an extensive body of knowledge in this area of research (Jackson, 1975, Zave and Jackson, 1997).
Even though their domain specific engineering approach does focus on software development, we think it can also be used to alter existing frameworks, processes and tools towards the requirements of a specific domain.
Research Methodology
Starting point of this research was an initiative, implemented through the CENTRAL EUROPE Programme co-financed by the ERDF, to foster innovation in SMEs across Europe. Since it was clear that cross-cultural differences will have to be faced, a research consortium had to be formed consisting of different universities and professional institutions from all the participating countries. The intent was to have not only the view from different researchers but also engage the local chambers of commerce to become regional catalysts for SMEs in their region.
During the proposal stage and the kick-off phase, it became evident that existing literature does not provide enough data for us to answer our research question. Hence, we developed a high-level research method.
The basic research model of our project consists of three fundamental pillars. The first pillar is based on an empirical study of160 small and medium-sized companies that were surveyed to illustrate the current ITSM and innovation situation in six Central European countries (Austria, Czech Republic, Germany, Hungary, Poland, and Slovakia).
The second pillar was based on 24 cases studies and a focus group of selected participants.
The third pillar is built on existing literature and frameworks, which have been thoroughly investigated and revised to find a best-of —breed solution for our domain specific ITSM method.
In order to cope with the different disciplines and information resources from literature, interviews, observations, and case studies, we decided to combine different research methods. Classification of accepted research methods can be done in different ways, the most common distinction is between qualitative research, quantitative research and triangulation. We utilized all three scientific approaches in order to tackle the rather complex and multi-disciplinary research project. However, the qualitative part has built the foundation of our research since qualitative research methods have become increasingly useful as the focus of information systems research shifts from technological to managerial and organizational issues(Klein and Myers, 1999, Myers, 2008, Mayring, 2000).
Engineering Process
Empirical Research to Screen the Domain
Since information on ITSM methods and models in the domain of SME is scarce, we had to collect relevant data on our own. Based on the findings in the literature, we developed a detailed survey which should answer important questions and guide further research steps. To gather the data, we set up an electronic survey in the mother tongues of each of the six different regions and asked the regional catalyst to contact SME of different sizes. Because of the scope of questions, we achieved a feedback rate of about 4% in average, which is quite usual for surveys of that size. For the data analysis we used different methods including descriptive, quantitative statistics as well as multivariate statistics like a regression analysis.
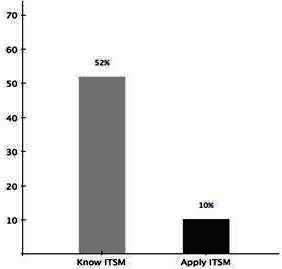
Fig 1. ITSM Awareness & Adoption
Besides other findings, the most crucial for our customized ITSM method is the actual awareness and utilization of ITSM frameworks across the different regions. Figure 1 shows the awareness of different frameworks and the implementation ratio of ITSM frameworks in SMEs.
As one can see, there is still a big gap between knowledge on ITSM frameworks and their application in Central European SME. In Fig 1 we can see, that only 52% of all SME are aware of ITSM frameworks such as ITIL, and less than 10% apply them. It is interesting that some of our results confirm findings from previous research (Szabo and Feher, 2010, Szabo and Feher, 2009, Broussard, 2008), thus, our data can be seen as representative. However, the reasons for these gaps seem to be different. After discussing this phenomenon with IT-department leaders of SME and other external experts, we can define different explanations:
- Missing awareness of productivity dimensions in IT departments: A lot of IT people are still seeing their tasks in maintaining given IT-functions and infrastructure, without measuring the value of their operations according to business processes. They are still not aware of the necessity to optimize their IT processes.
- Complexity of existing frameworks: A lot of IT department leaders mention that frameworks like ITIL or COBIT are too complex for them; they fear that such frameworks are an administrational overhead, which force them to document all steps they do comparable to the compliance topics they were forced to implement in the last 5 years.
The big gap between the awareness of ITSM methods and their application in Central European SMEs shows that ITSM as it exists now is not applicable for many SMEs. Maybe this is due to the missing awareness of the relevance of the topic or there is something wrong with the ITSM methods or the qualification process itself.
Another interesting fact, which is not shown in figure 1, is that almost all SMEs (48%) who are aware of ITSM frameworks did mention ITIL as one of the known frameworks. Therefore, we conclude that SME see ITIL as one of the most suitable, yet not fully applicable, ITSM frameworks. Hence, this framework will be focused on in a later stage of this research project (see chapter 4.3).
Qualitative Research
In order to create an IT system that should fit into an information system, instead of measuring the impact of an already existing information system to e.g. business process level, different methods should be used. Based on many rigorous vs. relevance discussions in the last decade, there is a consensus today that information systems consist more or less of the following: Task, Human and IT-System elements as shown in Fig 2(Heinrich and Sinz, 2002).
As a consequence, different research methods are needed to study the interaction between human beings and the business context (business task, business processes) they are working in, the interaction between human beings and the IT-System itself, and finally the fit between the IT-System (application, hardware, etc.) and the task context. Based on this IS-model, we choose a case study method to acquaint us with the application context of ITSM-methods in SME (H-T-relationship). Discussion of the case study results and co-design sessions about potential solutions with experts from the field should help us to get a consensually developed ITSM method as well as a task adequate to ITSM-modeling tool (IT-T-relationship).
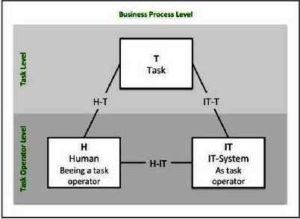
Fig2. IS-Model (T-H-IT Relationship)
Eventhough the survey gave us a rich set on empirical data, we realized that a preset of questions is unable to give us answers for the creation process of methods and technological systems that fit to the ITSM task context of IT department members in SME.
Case Studies
To understand the context in depth, we performed 24 case studies to analyze the current situation of small and medium-sized enterprises as well as to collect and share innovative examples of ITSM utilization between the regions. Each case presents the current situation, the problem and the specific solutions together with some background information about the company, which may allow classifying them in context. In other words, the case presents the story exactly as the protagonist has seen them, even with incomplete information, unclear answers and missing perspectives.
Each case study was conducted by a different mother tongue speaking research group; all followed a unified research paradigm as far as the cases have allowed this. In order to obtain comparable data, each case study provides three central parts:
- Description of the studied company
- Description of the business problem
- Description of the solution and the resulting experience
To obtain a diverse and representative collection of cases, the companies were selected according to different criteria: company size (number of employees, turnover, etc.), sector and region.
As a result of all case studies, we observed that in most cases the growth of IT-infrastructure, together with undefined procedures for incident requests of employees, lead to a stressful and error prone situation in the IT department. Realizing the contradiction between future growth and the weakness of the IT-organization, the management instructs the IT-department leader to make the IT-processes more efficient. There was interestingly no company available in our setting that chose the introduction of ITSM as a strategic option proactively and without external pressure. If we look at some of our cases, application of some elementary ITSM concepts led to quick wins for the company. However, most of them mentioned that once they started with their ITSM project they realized that:
- The existing ITSM frameworks are too complex.
- There are no guidelines available that deliver know-how about suitable introduction paths of ITSM.
Focus Groups
Based on the findings of the survey and case studies, we had a detailed view on domain specific business processes in SMEs and compared them with the existing IT Governance frameworks to get an idea in which area these frameworks tend to be too complex or less attractive for SME´s need. With support of selected experts out of the surveyed SME, we modeled detailed as-is processes utilizing ADOit. The challenges we encountered during the co-modeling phase gave us cognition on how ADOit should be customized to provide support for SMEs during the design and implementation phase of their ITSM processes. With this expert group, we also went into an evaluation phase to get an inter-subjectively discussed reliability of the identified drivers and barriers. This was a necessary step before we entered the creation phase of the SME-customized ITSM method and modeling tool.
Lessons Learned: Drivers & Barriers
From the survey and the case studies, the following lessons learned regarding drivers and barriers for an ITSM implementation have been identified as follows
Table1: Drives & Barriers in SMEs
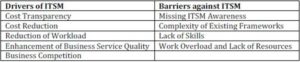
The identified barriers and drivers influence decision makers who must decide on the adoption and usage of ITSM. Thus, the drivers must be supported and highlighted by the prospective method. Drivers can be also addressed very well as motivation for potential users of the method.
Almost all of the barriers could be eliminated by a simplified and adjusted method. However, a particular problem is that even a single barrier can prevent a possible implementation project. Our approach was to address these barriers with a simplified ITSM method, which brings together business and IT strategy alignment, planning, implementation, operation and controlling of IT services in a very simple and modular way. From a methodological point of view, the support of drivers and the elimination of barriers in this domain are the basic creation targets on which the resulting method and tool-based implementation can be finally measured(Frank, 2010).
Development of a Simplified ITSM Method
The domain specific engineering (DSE) approach described in section 2.2 has been identified as an appropriate method to develop a domain specific ITSM method for SME since it was successfully applied in the Emergency Management domain in order to adapt IT Governance methods(Vogt et al., 2011). Consequently, we chose the DSE approach to develop a simplified ITSM method for SME and adapt the ADOit modeling tool (see section 4.4) accordingly.
Previous research has identified that IT Governance frameworks such as ITIL and COBIT are used in individual ways since different organizations have diverse motivations and needs. One way to tackle this problem is to build metamodels and identify recurring patterns, which lead to a better understanding of causes and effects(Looso and Goeken, 2010).
In order to build a domain specific ITSM method, we had to get to know the domain’s needs, identify their barriers and follow a suitable requirements engineering method. Our approach to design a domain specific ITSM model is shown in Figure 3.
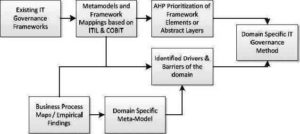
Fig 3. Engineering Process
ITIL and COBIT metamodels, as well as framework mappings, were taken from previous research projects, which also dealt with IT Governance metamodeling and application issues(Looso and Goeken, 2010, Goeken and Alter, 2009, Goeken et al., 2009, IT Service Management Forum, 2008).
In order to address the drivers and tackle the barriers, we had to develop an ITSM method that should be simple enough to be accepted by SME, but yet universal enough to support their business. Since ITIL and COBIT are proved frameworks in large enterprises, we had a look at their processes and controlled objectives and chose a “best of breed” approach from the two frameworks. Again the focus group turned out as a most valuable information source. Iterative discussions and the use of AHP as described below gave us a starting point for the simplified ITSM method and the resulting metamodel. The suggested method will not serve as an additional ITSM framework; it is rather a model that is upwards compatible with ITIL and COBIT. This approach guarantees flexibility for SMEs to migrate to a larger framework when their companies grow and need more rigor to manage their IT services. Key goals were:
- Provision of a ‘cookbook’ about ITSM explaining the different patterns in a framework in a neutral and easy understandable way.
- Modularization and simplification of common patterns of various ITSM frameworks and methods.
- Definition of a possible implementation process and explanation of the “best of breed” approach to select, adapt and adopt existing frameworks.
- Delivery of ITSM training approach tailored for SMEs.
To identify the most important COBIT ‘control objectives’ and ITIL ‘best practices’, we had to prioritize their impact on the domain specific business processes. In order to do this, we utilized decision making methods based on AHP (Analytical Hierarchy Process).
AHP is a decision support method to simplify complex decisions and make rational decisions. The AHP-Method is “hierarchical”, because the criteria which are used to solve a problem are in a hierarchical order. Elements of a hierarchy can be divided into groups, to refine and simplify the decision-making process.
It is “analytical” because it describes and analyses the constellation and dependencies of the particular problem and it is a “process” because it follows a defined and repeatable procedure. Therefore, AHP supports decisions in teams to find joint solutions while it provides transparency of the process and minimized inconsistencies in decisions (e.g. A > B, B > C, but C > A). It enhances “gut decisions” by a qualitative weighting based on comparative decisions (Saaty, 1990, Saaty, 1987).
Figure 4 will illustrate how we utilized AHP in the engineering process.
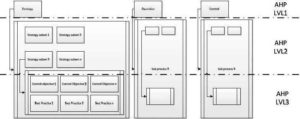
Fig 4. AHP Approach
By the means of AHP, we were able to separate necessary and useful ‘control objectives’ and ‘best practices processes’ from ‘expendable practices and controls’. ‘Expendable practices and controls’ are not to be seen as useless, we believe that all elements in COBIT and ITIL are useful and have to be considered during a maturity process, however, in order to simplify a method and make it more flexible, we had to identify the most suitable parts as shown in Figure 4.
Figure 5 shows the implementation of these concepts. The shown prioritisation is highly pragmatic and, in this case, contains only the distinction between mandatory (shown in dark shades) and optional modules (shown in light shades). In order to address even the smallest SMEs, we had to assume that individual companies have carried out a complete outsourcing of their IT. However, implementing the mandatory modules is useful even in these cases. The mandatory modules provide the basis for successful use of ITSM.
The optional modules supplement them. To utilise all the added value that can be provided by using ITSM, all modules should be considered. The selection of modules depends to a great extent on the company and its facets, the strategy and requirements. Hence, the shown prioritization reflects only the minimum required implementation strategy for SMEs.
The module map shown in figure 5 structures the available modules in three levels. Strategic Planning, the top horizontal level combines both strategic and tactical aspects of IT Service Management. The distinctive feature of the activities is the relatively long time horizon they take into account.
The addressed aspects provide the framework in which the operational activities can take place. The bottom horizontal level — service operations — describes the operation of services and thus the everyday business of IT. The conclusion is the chapter Monitoring, Improvement and Change. As shown vertically on the map of the ITSM modules, this chapter discusses the across-the-board issues that involve both strategy and tactics as well as operational effectiveness.
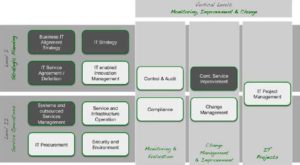
Fig5. Modules of the Simplified ITSM Method
Domain Specific Customizing of ADOit
Within the project ADOit, an IT-Management modeling tool, is used for the strategic, tactical and operational management of the entire IT of an enterprise. It covers all layers that are necessary for a holistic view from IT strategy down to operation of IT: strategy, business processes (only high-level), service portfolio, applications, software, IT infrastructure and IT service processes (BOC-Group, 2011). The software is a fundamental part of the concept to increase the awareness on ITSM in small and medium-sized enterprises. The two main applications are the enterprise architecture management and ITSM. ADOit can, therefore, be assumed as a visual configuration management database, which can easily be used by non-IT personnel.
Adapting ADOit Metamodel to Simplified ITSM Method
“A study about language is spoken in language”. Discussions about language require a further sematic level: a meta-language. The investigation of models is very similar and requires a metamodel. The metamodel can be assumed as a model of a modeling language. This behavior is recursive and accordingly the subsequent logical level is a meta-metamodel (and so on meta3model, metanmodel) (cf.Fig 6 inspired by(Strahringer, 1996)). In other words, on the one hand a high-level model of multiple modeling languages can be defined. The other hand, several modeling languages – which all have certain similarities — can be derived from a meta-model(Karagiannis and Kühn, 2002, Strahringer, 1996).The current metamodel of ADOit (cf. Fig 8) is specific for the IT domain. It reflects all possible requirements of COBIT and ITIL. By covering the wide range of requirements, the current metamodel is powerful, but at the same time very complex.
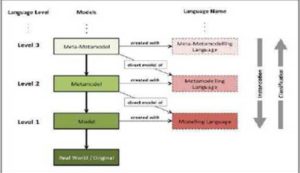
Fig 6. Metamodeling Terminology
Figure 7 shows the requirement engineering process as a whole, as well as the dependencies and influences of the sources / stakeholders on the deliverables.
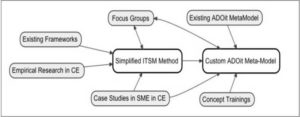
Fig7. Requirement Engineering Process
Based on the results of the previous research, a primary goal was to reduce the complexity of the tool. However, the requirements from the following sources were considered necessary for the adaption of the existing metamodel:
- The use case modeling experience has been considered. For example, we have identified that the information systems in observed SMEs are less complex and for that reason the application architecture is sufficient for the documentation or in other words, the software architecture could be eliminated.
- The simplified ITSM method (cf. chapter 4.3) has been reflected to ensure the future applicability to all modules of the method.
- The tool is a fundamental part of the training to boost awareness for IT Service Management. A detailed temporal dimension is not considered a relevant and temporal scale containing two values [as-is; to-be] is sufficient. The intermediate steps of a transformation project are not relevant for the training purpose and consistently the model type “Project” is no longer applicable.
- The focus groups have been used as a validation instance to ensure the practicality of the developed solution.
Listing each request and the related adjustment is beyond the scope of this document. Accordingly, only the used approaches to adapt the metamodel are mentioned:
- Elimination of complete model types
- Merge of multiple model types to one model type (IT Service Business Process Architecture, see dotted box in Figure 9)
- Elimination of objects within a model as well as the elimination of compulsive relations
The result of these adjustments is a customized metamodel for ITSM in SME. Since the metamodel provides now less features, the degree of complexity has decreased significantly and therefore, it is more suitable for the application in small and medium-sized enterprises (see Fig. 9)
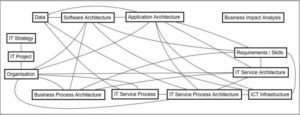
Fig8. Original “Complex” ADOit Metamodel (Excerpt cf. (Karagiannis))
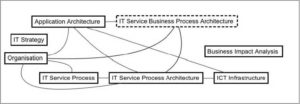
Fig.9. Customized“Simplified” ADOit Metamodel (Excerpt)
Expert Evaluation of the “simplified” ADOit Version
The first release of the customized ADOit version includes the major changes of the metamodel as shown in Figure 9. To gain feedback of this version, a group of IT Service Management experts containing different roles has been invited to a workshop:
- IT Department leads of medium-sized companies & public institutions implementing ITSM
- Members of itSMF / ITSM & ITIL Experts
- Professors with ITSM, IT project management, process management or IT controlling background.
The goal of this evaluation was to identify major issues regarding the concept or the implementation of the concept in ADOit, as well as to evaluate its usability and applicability compared to existing ITSM methods and tools.
The test group has been asked different questions about the completeness, applicability and usability of the customization. For the basic understanding it is required to define the two elements “model types” and “classes”. A model type is a collection of elements like classes and relations. For example, the model type IT service process contains the classes activity, decision, etc. and aims to provide the option to model a process within the IT.
The participants have been asked if the amount of classes is too less, ideal or to less. Most participants indicate that the available classes of the different models in ADOit are enough for the purposes of SMEs (see Fig 10). Model type Organisation and IT Service Process Architecture are seen as ideal by all participants. Only some participants indicate that the other types provide too less classes (e.g. missing class “Cloud” in ICT Infrastructure). Nobody indicates that too many classes are available.
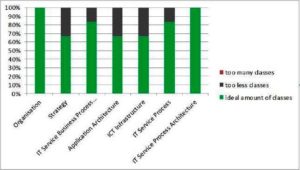
Fig 10. Amount of Classes per Model Type
The usability and clarity of the single model types can be seen as “ok” in average (see Fig 11). The relative homogenous result (minimal 14%, maximum 28% for “ideal” and no “poor”) between the different model types is also reflected in the overall usability of our tool (see Fig 14).
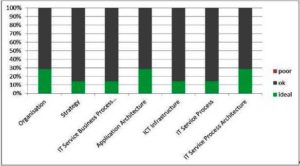
Fig 11.Usability and Clarity per Model Type
As part of the specification and with focus on simplification, some model types (e.g. Project) have been hidden from the set of available model types via a “model type filter”. Accordingly, the participants have been asked if they would miss these model types for the usage in SMEs. The result (Fig 12) shows that only the model type “Project” might have a significant relevance for SME. The result confirms our approach to hide models instead of removing them finally. Using the filter “All model types” every existing model type in ADOit will be displayed and can be used.
As already mentioned, one of the main goals was to reduce the complexity of the tool. Accordingly, a worthy indicator for us is whether the model types are sufficient (Fig 13 — left chart) or whether too many model types are available (Fig 13 — right chart). In the first chart, a clear majority of the participants assumed that the remaining model types are sufficient. Even all the participants confirmed that there are not too many model types. So as a conclusion, the simplification was successful, but a further reduction does not make sense. There is a risk of a kind of oversimplification.
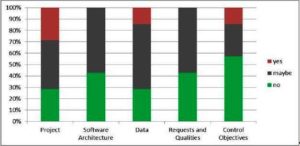
Fig 12. Relevance of Hidden Model Types
So far, the individual model types have been considered separately from each other. Finally, the entire suite has been evaluated in three categories (1) distinctness of the elements (classes, relations, etc.), (2) clarity and (3) usability. In Fig 14 we can see, that over 50% of the participants rate the three criterions with “good”. The criterion of “distinctness of elements” was explicitly addressed in the specification and some classes have been visualized differently (e.g. color). Accordingly, all participants rated this criterion as “ok” or even better.
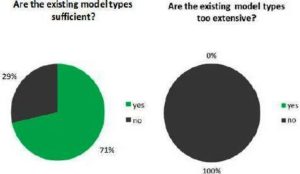
Fig 13. Sufficiency and Extensiveness of Existing Model Types
The figure shows also, that in criteria of “Clarity” and “Usability” there is space for improvement. Within the project, we will address these weaknesses through an improved introduction to the tool. A future research project could implement a simple maturity model and a “stage based” implementation plan for SMEs to increase the usability clarity even more.
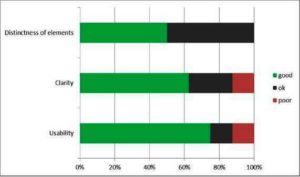
Fig 14.Overall rating of Distinctness, Clarity and Usability
Limitations and Future Research
The final version of the customized ADOit tool and a detailed description are not fully available yet to the public. However, the final tool including an online training platform will be freely available to the public beginning of 2012 via http://www.innotrain-it.eu
The full roll-out of the proposed ITSM method to SMEs is still in progress, thus the above shown results reflect the findings until today. Therefore, we are unsure how the customization of ADOit and the simplified ITSM methods will be accepted by the final users. Nonetheless, the current results have been discussed with a user focus group to evaluate its applicability and usability. In general all experts and members of the focus group agree that the approach seems very promising and valuable for SMEs.
Due to financial limitations and time constraints we did not implement any maturity models in our current project. However, we strongly encourage future research to focus on this issue.
Conclusion
The results of our own survey and case studies as well as our literature review have shown that although there is a strong awareness of ITSM in SMEs, a suitable method to implement ITSM was missing and therefore the general application of ITSM in SMEs is rather low as shown in chapter 4.1.
We have researched the domain of SMEs thoroughly in order to define their requirements and needs. With our research we highlighted the implementation barriers and ITSM opportunities. The sum of these preliminary results enabled us to design a simplified ITSM method, particularly tailored towards the capabilities of SMEs. As a result, we were able to customize a BPM tool and utilized it during several stages of our project.
We believe that the simplified ITSM method in combination with the customized BPM tool (ADOit) provide valuable methods and tools that can be applied easily in most SMEs.
Acknowledgement
The mentioned project INNOTRAIN IT is implemented through the CENTRAL EUROPE Programme co-financed by the ERDF. We thank all participating organizations and contributors for their time and support.
References
Bhattacharjya, J. & Chang, V. (2007). “Evolving IT Governance Practices for Aligning IT with Business – A Case Study in an Australian Institution of Higher Education,” Journal of Information Science and Technology (JIST), 4 (1), 24-46.
Publisher – Google Scholar
Bjorner, D. (2010). ‘Domain Engineering,’ In Boca, P., Bowen, J. P. And Siddiqi, J., Eds., Formal Methods: State of the Art and New Directions, Springer London, 1-41.
BOC-Group (2011). “Adoit – IT-Architektur- und -Servicemanagement,” [Online], [Retrieved February 20th, 2011],http://www.boc-group.com/de/produkte/adoit/
Publisher
Broussard, F. W. (2008). “IT Service Management Needs and Adoption Trends: An Analysis of a Global Survey of IT Executives,” IDC Whitepaper, IDC Research, Unpublished.
Publisher – Google Scholar
Frank, U. (2010). “Zur Methodischen Fundierung Der Forschung in Der Wirtschaftsinformatik,“ in Österle, H., Winter, R. and Brenner, W., Eds., Gestaltungsorientierte Wirtschaftsinformatik: Ein Plädoyer Für Rigor und Relevanz, Infowerk, St. Gallen / Nürnberg, 35-44.
Publisher – Google Scholar
Goeken, M. & Alter, S. (2009). “Towards Conceptual Metamodeling of IT Governance Frameworks Approach – Use – Benefits,” in Stefanie, A., Ed. 42nd Hawaii International Conference on System Sciences, 2009.1-10.
Publisher – Google Scholar
Goeken, M., Alter, S., Milicevic, D. & Patas, J. (2009). “Metamodelle Von Referenzmodellen Am Beispiel ITIL: Vorgehen, Nutzen, Anwendung,“ Lecture Notes in Informatics (LNI), P-154, 473-481.
Publisher – Google Scholar
Heinrich, L. & Andsinz, E. (2002). ‘Wirtschaftsinformatik,’ in Rechenberg, P. Andpomberger, G., Eds., Informatik-Handbuch, Hanser Verlag, Munich, Germany.
INNOTRAIN-IT (2011). “INNOTRAIN IT — Learn How to Simplify Your IT!,” [Online], [Retrieved Feb. 6th, 2011],http://www.innotrain-it.eu/
Publisher
IT Governance Institute, I. T. G. I. (2003). Board Briefing on IT Governance, 2nd Edition, Rolling Meadows, Illinois, USA: Unpublished.
Publisher
IT Servicemanagement Forum (2008). ITIL-COBIT-Mapping: Gemeinsamkeiten und Unterschiede Der IT-Standards,Symposion Publishing.
Publisher – Google Scholar
Jackson, M. A. (1975). Principles of Program Design, Academic Press, Inc., Orlando, FL, USA.
Publisher – Google Scholar
Karagiannis, D. ‘Informationssystemeinfrastruktur,’ Department for Knowledge & Business Engineering (DKE),University of Vienna.
Karagiannis, D. & Kühn, H. (2002). “Metamodelling Platforms,” Third International Conference Ecweb — Dexa 2002, LNCS 2455.
Publisher – Google Scholar – British Library Direct
Klein, H. K. & Myers, M. D. (1999). “A Set of Principles for Conducting and Evaluating Interpretive Field Studies in Information Systems,” MIS Quarterly Executive, 23 (1), 67-93.
Publisher – Google Scholar – British Library Direct
Levy, M. & Powell, P. (2005). Strategies for Growth in Smes – the Role of Information and Information Systems, Elsevier Butterworth-Heinemann, Burlington, UK.
Publisher – Google Scholar
Looso, S. & Goeken, M. (2010). “Application of Best-Practice Reference Models of IT Governance,” in Proceedings of 18th European Conference on Information Systems (ECIS), Pretoria, South Africa.
Publisher – Google Scholar
Luftman, J. & Kempaiah, R. (2007). “An Update on Business-IT Alignment: A Line Has Been Drawn,” MIS Quarterly Executive, 6 (3), 165-177.
Publisher – Google Scholar
Mayring, P. (2000). “Qualitative Inhaltsanalyse,” Grundfragen und Techniken, Deutscher Studien Verlag, Weinheim, Germany.
Publisher – Google Scholar
Myers, M. D. (2008). “Qualitative Research in Information Systems,” Updated Version, MIS Quarterly. [Online], [Retrieved June 24, 2009], http://www.qual.auckland.ac.nz/
Publisher
OECD (1993). Small and Medium-Sized Enterprises: Technology and Competitiveness, OECD Publishing, Paris.
Publisher
OECD (2010). Smes, Entrepreneurship and Innovation, OECD Publishing, Paris.
Publisher – Google Scholar
Peterson, R. R. (2004). “Integration Strategies and Tactics for Information Technology Governance,” in Van Grembergen, W., Ed. Strategies for Information Technology Governance, Idea Group Publishing, Hershey, Pa., 37 – 80.
Publisher – Google Scholar
Saaty, T. L. (1987). “Rank Generation, Preservation, and Reversal in the Analytic Hierarchy Decision Process,” Decision Sciences, 18, 157-177.
Publisher – Google Scholar
Saaty, T. L. (1990). “How to Make a Decision: The Analytical Hierarchy Process (AHP),” European Journal of Operational Research.
Publisher – Google Scholar
Schäfer, G., Hertweck, D. & Strolz, G. (2008). ‘IT-Compliance im mittelstand,’ in Hildebrand, K. and Meinhardt, S., Eds.,Compliance & Risk Management, Dpunkt.Verlag, 71-79.
Google Scholar
Shapiro, C. & Varian, H. R. (1998). Information Rules: a Strategic Guide to the Network Economy, Harvard Business School Press.
Publisher – Google Scholar
Strahringer, S. (1996). “Metamodellierung Als Instrument des Methodenvergleichs: Eine Evaluierung Am Beispiel Objektorientierter Analysemethoden,” Shaker, Aachen.
Publisher – Google Scholar
Szabo, Z. & Feher, P. (2009). “Current Challenges of IT Service Management in Hungary,” in Conference Proceedings of CONFENIS 2009, Gyor, Hungary, 10 Pages.
Publisher – Google Scholar
Szabo, Z. & Feher, P. (2010). “Management of IT Services- A Snapshot on Hungary,” in Savino, M. and Chakpitak, N., Eds., Proceedings of 4th International Conference on Software, Knowledge, Information Management and Applications – SKIMA 2010, Paro, Bhutan, 8 Pages.
Publisher – Google Scholar
Van Grembergen, W. & De Haes, S. (2009). Enterprise Governance of Information Technology: Achieving Strategic Alignment and Value, Springer, New York.
Publisher – Google Scholar
Van Grembergen, W., De Haes, S. & Guldentops, E. (2003). Structures, Processes and Relational Mechanisms for IT Governance, in Van Grembergen, W., Ed. Strategies for Information Technology Governance, Idea Group Publishing, Hershey, Pa., 1 – 36.
Publisher – Google Scholar
Vogt, M., Küller, P., Hertweck, D. & Hales, K. (2011). “Adapting IT Governance Frameworks using Domain Specific Requirements Methods: Examples from Small & Medium Enterprises and Emergency Management,” in Americas Conference on Information Systems (AMCIS), 2011 Detroit, MI, USA. Association for Information Systems (AIS), Paper 481.
Publisher – Google Scholar
Zave, P. & Jackson, M. (1997). “Four Dark Corners of Requirements Engineering,” ACM Trans. Softw. Eng. Methodol., 6 (1), 1-30.
Publisher – Google Scholar – British Library Direct

















