Introduction
Various tools and solutions to help organizations to maximize the use of IT have been given from the academic and professional world. But these tools have limitations in the context of SMEs. On the one hand, the proposed instruments provide little information about the problems and their causes within an organization (Ciborra, 1997).
On the other hand, these instruments have been designed mostly for large companies. Indeed, in the literature there is a strong bias towards this kind of firms (Burgess, 2002). So, it is needed more researching that helps to solve the real IT problems that SMEs have.
Action-research (AR) is a methodology that allows the researcher to build theory, while simultaneously assisting the organization to solve its real problems. Kaplan (1998) used AR to create the well-known activity-based costing and balanced scorecard (BSC). Because of its advantages, we investigated the effective use of IT in SMEs using AR. Consequently, this research had two objectives: (a) researching the IT problems that affect SMEs, and (b) contributing to information systems research by applying a little explored methodological paradigm. The methodology was applied to a total of nine companies: four from New Zealand, three from Colombia and two from Chile. The companies’ size varied between three and 20 employees.
The remainder of this article summarizes the preliminary results of this research and is divided in four sections. Section two summarizes the theoretical background and presents the questions that we decided to study using AR. Section three explains the main aspects of AR. Section four briefly describes how the methodology was developed following the principles of AR and the most relevant results obtained, and section five presents and discusses our conclusions.
Theoretical Background
Despite the significant technological and economic differences between countries, it can be argued that SMEs have some common problems (Alarcón et al., 2002, Arellano et al., 1991, Montazemi, 2006, Sharma et al., 2006). In general, it can be mentioned three factors that affect the effective use of IT in the enterprise: (a) limited IT skills and resources (Levy et al., 2005), (b) lack of a strategic plan or an incomplete execution of it (Blili et al., 1993, Levy et al., 2000, Burgess, 2002, Chan et al., 2007) and (c) the emphasis on the operation (Cragg et al., 2007, Montazemi, 2006).
One of the characteristics of SMEs is the shortage of resources, particularly IT. For instance, Montazemi (2006) claimed that SMEs in the U.S. and Canada had a centralized structure, preferring to recruit generalist rather than specialist staff. Furthermore, he concluded that SMEs had few resources to invest, particularly in IT, leaving little capacity to absorb the costs of a bad investment in technology. Obviously, the lack of IT mean that systems purchased are not best suited to the needs of the enterprise or that they are not used optimally. In fact, Levy et al (2005) concluded that the lack of specific knowledge affects the use of IT in SMEs.
Another aspect that affects the proper use of IT is the absence of a strategy. Several authors have shown that SMEs do not have a defined strategy or execution. For example, Blili et al (1993) differentiated SMEs of large companies in five dimensions, one of them was its organizational informality. More recently, other authors have argued that SMEs don’t have formal planning and control methodology (Levy et al., 2000, Boehme et al., 2007, Burgess, 2002). The absence of a strategy affects the alignment of IT; Chan et al (2007) for example, stated that IT alignment is not possible if the business strategy isn’t known or it is underway. The authors concluded that companies structurally more sophisticated tend to use more complex systems and achieve better performance.
The emphasis on the operation affects the optimal use of IT in SMEs. According to Levy et al (2005), orientation to operational aspects made managers focused on deliveries at the expense of systems that help to manage the business. On the other hand, Cragg et al. (2007) concluded that SMEs tend to be more aligned to the operational level than to the strategic one. Finally, Montazemi (2006) concluded that the emphasis on operation, limited technical skills of the staff and restricted resources meant that, cause these companies were less willing to invest in IT.
In SMEs, these problems affect the use of IT in two ways. First, they have an incomplete portfolio of computer applications, in other words, some necessities of the enterprise could be solved with a specific application but it is not among those already exists in the company. For example, we saw often that some managers liked having a system to monitor the performance of the organization, for example a BSC. There are several good BSC systems on the market, but they still have not purchased anyone.
Second, another problem for SMEs is the inefficient use of IT because some needs of the enterprise could be solved using systems already existing, by increasing their current use. This situation is common into SMEs and it is reported in the literature. For example, Sharma and Bhagwat (2006) concluded “With insufficient managerial and technical skills, and the lack of funds to acquire such skills, smaller organizations often implement IS in a less than optimal way.” More empirically, many small organizations have systems that are not operated at a maximum level, implicitly producing losses and inefficiencies.
As consequence, we explored two questions regard to the problems of IT into SMEs:
Q1: Does SME have incomplete portfolio of computer applications?
Q2: Does SME have systems used inefficiently?
The answer to the first question (Q1) would help us find out what new systems are necessary in SMEs and the answer to the second question (Q2) would help us find out problems with the inefficient usage of existing IT.
The Action-research Methodology
Action research is a methodology where the researchers and participants work together to diagnose a problem and develop a solution. The process of collaboration brings mutual benefits for the researcher and the organization. On the one hand, the organization gets a solution to a problem that has, while on the other hand the researcher gets to increase the body of existing knowledge about the studied phenomena (Kock et al., 1997).
There is no a single definition of what action research is, but some basic elements seem to arise from different authors. Bryman et al (2007), for example, show that in action research the research implicates real problems within the organization; also it involves an iterative process of problem identification, planning, action and evaluation; moreover, action research leads to the re-education or changing patterns of action; and finally, it seeks to contribute to both academic theory and practicable action (Collis et al., 2003). Kemmis et al (2005) conceived AR as a spiral of activities: planning; action and observation; reflection; review and planning; and then start a new cycle (Figure 1).
Particularly in information systems research, action research presents opportunities that could help to improve the practice and theory, increasing knowledge about the discipline (Baskerville et al., 2004). For example, a research based on action research fits very well to understand the process of adoption of software in business. However, in the case of information systems research, there have been several calls to use action research to a greater amount (Baskerville et al., 2004, Avison et al., 1999, DeLuca et al., 2007).
Methodology Applied in this Research
AR comes from a robust scientific background. The research model applied in this research was based on the general model shown in Figure 1, where each company was transformed through a cycle of AR.
We used a case study approach to collect the data. At the end of each cycle, when it was needed, new improvements to the AR investigation methodology were included until a saturation point was achieved. The saturation point is a stage of a qualitative research where new cases do not provide any more information (Bryman et al., 2007). The saturation point was achieved after the fourth case. One day was the minimum time spent in each company in applying the AR methodology.
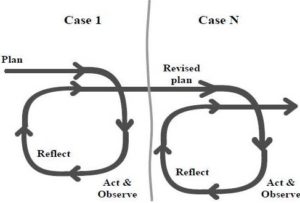
Fig 1. The Action Research Model Used in This Research Adapted of Kemmis et al (2005)
Following recommendations of several authors (Bryman et al., 2007, Checkland et al., 2007, DeLuca et al., 2007, Greenwood et al., 2007), three ways were used to validate the methodology: collection of different type of data, multiples observers and participant validation. Data were collected from: semi-structured interviews to key informants, work-observation, rich-pictures, archival, questionnaires and webpage analysis. Additionally, two members of the team interviewed each participant. At least, two key informants were interviewed: the owner-manager and a key worker selected by him/her. Sometimes a third key informant was interviewed as well.
At the end of each visit, the research team presented its findings and recommendations to the participants. Then, the participants were asked to evaluate these conclusions. Validation by participants has been suggested as an appropriate form of validity in qualitative research (Bryman et al., 2007, Yoong et al., 2007, Bryman, 1988). Figure 2 shows the activities performed in each company by the researchers.
The remainder of this section is divided in two sub-sections. The first subsection informs about the main discovering of this research. The second subsection presents the results of the participant validation.
Results
During the research, nine companies were analyzed. The companies were from New Zealand, Colombia and Chile. These companies and countries were selected due to the implementation of a major research project. On one hand, New Zealand companies belonged to an industrial cluster, while Colombia and Chile firms were selected through personal contacts of one of the authors. Table 1 summarizes the background of case firms (due to confidentiality agreements, companies’ identity are not disclosure).
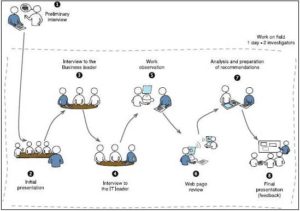
Fig 2. Activities Performed by Researchers in Each Company
The findings showed that all cases presented evidence supporting that SMEs have two type of IT problems: incomplete portfolio of applications (Q1) and inefficient use of IT (Q2). Table 2 counts the number of problems detected classified according to Q1 and Q2. The table shows that all cases presented evidence supporting both questions. However, two different sort of inefficiency were found: organizations that underutilize existing system and organizations that use more than one system to manage one single kind of data.
Table 1: Cases Background

Table 2: Number of IT Problems Identified and Classified According to Q1 and Q2
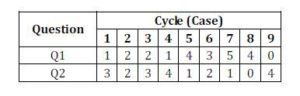
New Zealand (case 1-4) businesses had a more complete portfolio of IT applications, but at the same time were those that showed a greater number of inefficient uses of IT. Possibly an explanation for this advantage of New Zealand companies over Latin-American and New Zealand businesses would be the hiring of external IT consultants.
In addition, two clusters of companies appeared when the most often IT problems were identified and classified. The first was the group of companies that had mainly very basic IT deficiencies, e.g., lack of data backup. A second cluster was constituted of companies that had mainly problems with more advanced systems, e.g., document management system. Latin-American businesses (case 4-9) were in the first group and New Zealand companies in the second one. Also, an unexpected finding emerged from the research. Common issues of IT usage were discovered among the companies despite the diversity of cases.
Participants’ Validation
As it was explained previously, a feedback from participants at the end of each session was included. Each answered three questions:
- “Using a scale of 1 to 10, how useful do you think the recommendations were?” “What would you improve of the methodology?” and
- “Would you recommend us to another organization?”
These questions were interrelated between them to valid the responses of each participant. To avoid bias among participants, since the second case onwards, the participants answered all three questions in secret and then show their answers to the audience. Then, the investigators asked them to substantiate their answers.
We previously defined that to get the saturation point, the feedback should achieve the maximum evaluation points (i.e. 10) in a sequence of cases. Otherwise new improvements should be made to the procedure depicted on Figure 2. Figure 3 shows the evolution of the score for each case. After the fourth case, all participants validated our conclusions at 100% of certainty.
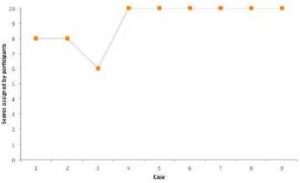
Fig 3. Participants’ Feedback Evolution
We expected the feedback would evolve positively as we conducted more action research cycles. For example, when researchers asked the case 4’s manager how accurately she thought the recommendations had been, she said: “I’d say 100% accuracy, so 10 [out of 10]…we know we have stuff that is not working and I think you identified it and gave us solutions.” Similar comments made other managers. Case 8’s manager said “10. First because the problems that I have, you describe them. Everything was well organized, all I have to do ¡and I’m going to do it, because I must do it if I want to improve! You said it clearly. I could realise about the problems that the company has.”
Conclusions
This research confirmed that AR is a useful framework for system researchers. This methodology remains little explored in the field of information systems (Baskerville et al., 2004, Avison et al., 1999, DeLuca et al., 2007). Although a limitation of this study was that researchers could not get more involved in cases, this research is a contribution to the advancement of AR, and it is hoped that other researchers will be encouraged to use this type of methodology. This research met the four criteria proposed by Figueiredo et al (2007) about the AR outcomes. Some participants’ comments are testimony of that. For example a manager e-mailed us: “Thanks for all your help. I enjoyed learning about how we can, quite simply, enhance our business”. Another manager said: “you have done a lot of hard work to analyze me as a manager of this company. Your conclusions really are the Achilles heel that we have currently”. Ultimately, researchers and practitioners could use the process developed in Figure 2 as a methodological framework to identify the IT problems in a SME.
References
Alarcón, C. & Stumpo, G. (2000). ‘Pequeñas y Medianas Empresas Industriales en Chile. Santiago,’ CEPAL, División De Desarrollo Productivo y Empresarial.
Google Scholar
Arellano, R., D’ Amboise, G. & Gasse, Y. (1991). “Administrative Characteristics and Performance of Small and Medium-Sized Businesses in a Developing Country,” Entrepreneurship & Regional Development, 3 (4), 317-334.
Publisher – Google Scholar
Avison, D., Lau, F., Myers, M. & Nielsen, P. A. (1999). “Action Research,” Communications of the ACM, 42 (1), 94-97.
Publisher – Google Scholar – British Library Direct
Baskerville, R. & Myers, M. D. (2004). “Special Issue on Action Research in Information Systems: Making IS Research Relevant to Practice,” MIS Quarterly, 28 (3), 329-335.
Publisher – Google Scholar – British Library Direct
Blili, S. & Raymond, L. (1993). “Information Technology: Threats and Opportunities for Small and Medium-Sized Enterprises,” International Journal of Information Management, 13 (6), 439-448.
Publisher – Google Scholar – British Library Direct
Boehme, T., Ma, Y. X., Childerhouse, P., Corner, J., Seuring, S., Basnet, C. & Deakins, E. (2007). “The Application of the Quick Scan Audit Methodology in SME’s,” Proceedings of the Small Enterprise Conference, Building Sustainable Growth in Smes, 23-26 September, Manukau City, New Zealand, 1-12.
Publisher – Google Scholar
Bryman, A. (1988). “Quantity and Quality in Social Research,” Routledge, London.
Publisher – Google Scholar
Bryman, A. & Bell, E. (2007). ‘Business Research Methods,’ Oxford University Press, USA.
Publisher – Google Scholar
Burgess, S. (2002). ‘Managing Information Technology in Small Business: Challenges and Solutions,’ Introduction, Managing Information Technology in Small Business: Challenges and Solutions, Burgess, S. (Ed), IGI Global.
Publisher – Google Scholar
Chan, Y. E. & Reich, B. H. (2007). “IT Alignment: What Have We Learned?,” Journal of Information Technology, 22 (4), 297-315.
Publisher – Google Scholar – British Library Direct
Checkland, P. & Holwell, S. (2007). ‘Action Research, Information Systems Action Research,’ Kock, N. (Ed), Springer US.
Ciborra, C. U. (1997). “De Profundis? Deconstructing the Concept of Strategic Alignment,” Scandinavian Journal of Information Systems, 9 (1), 67-82.
Publisher – Google Scholar – British Library Direct
Collis, J. & Hussey, R. (2003). ‘Business Research: A Practical Guide for Undergraduate and Postgraduate Students,’Palgrave Macmillan, Hampshire, New York.
Google Scholar
Cragg, P., Tagliavini, M. & Mills, A. (2007). “Evaluating the Alignment of IT with Business Processes in SMEs,” 18th Australasian Conference on Information Systems (ACIS 2007). Proceedings of the 18th Australasian Conference on Information Systems Ed. Toowoomba, University of Southern Queensland.
Publisher – Google Scholar
DeLuca, D. & Kock, N. (2007). “Publishing Information Systems Action Research for a Positivist Audience,”Communications of the Association for Information Systems, 19 (1), 10.
Publisher – Google Scholar
Figueiredo, A. & Cunha, P. (2007). “Action Research and Design in Information Systems,” Information Systems Action Research, Kock, N. (Ed), Springer US.
Publisher – Google Scholar
Greenwood, D. & Levin, M. (2007). ‘Introduction to Action Research. Social Research for Social Change,’ Sage Publications Inc., Thousand Oaks, CA.
Publisher
Kaplan, R. S. (1998). “Innovation Action Research: Creating New Management Theory and Practice,” Journal of Management Accounting Research, 10, 89-118.
Publisher – Google Scholar – British Library Direct
Kemmis, S. & McTaggart, R. (2005). ‘Communicative Action and the Public Sphere,’ the Sage Handbook of Qualitative Research, Lincoln, Y. & Denzin, N. (Ed), Sage.
Publisher – Google Scholar
Kock, N. F., McQueen, R. J. & Scott, J. L. (1997). “Can Action Research Be Made More Rigorous in a Positivist Sense? The Contribution of an Iterative Approach,” Journal of Systems and Information Technology, 1 (1), 1-23.
Publisher – Google Scholar
Levy, M. & Powell, P. (2000). “Information Systems Strategy for Small and Medium Sized Enterprises: An Organisational Perspective,” Journal of Strategic Information Systems, 9 (1), 63-84.
Publisher – Google Scholar
Levy, M. & Powell, P. (2005). “Strategies for Growth in SMEs: The Role of Information and Information Systems,”Butterworth-Heinemann, United Kingdom.
Publisher
Montazemi, A. R. (2006). “How They Manage IT: SMEs in Canada and the U.S,” Commun. ACM, 49 (12), 109-112.
Publisher – Google Scholar – British Library Direct
Sharma, M. K. & Bhagwat, R. (2006). “Performance Measurements in the Implementation of Information Systems in Small and Medium-Sized Enterprises: A Framework and Empirical Analysis,” Measuring Business Excellence, 10 (4), 8-21.
Publisher – Google Scholar – British Library Direct
Yoong, P., Pauleen, D. & Gallupe, B. (2007). “Generating Data for Research on Emerging Technologies,” Information Systems Action Research, Kock, N. (Ed), Springer US.
Publisher – Google Scholar







