Robustness
The robustness of this technique is checked by applying different types of attacks on the watermarked images. Results show that our technique is robust against most of the attacks because watermark can still be detected after applying different types of attacks.
Filtering Attacks:
For testing purpose the watermark image is attacked with a low pass filter and median filter, each with window sizes from 2×2 to 6×6, and Wiener filter. Watermark is detected after each attack which shows the technique is robust to these types of attacks.
Noise Attack:
The other type of attack carried out is Gaussian noise addition with window size 3×3 and STD of 0.2, also noise with power of 500,1000,5000,10000, and 15000 was added and original watermark is detected from the corrupted images.
JPEG Compression Attack:
Compression of watermark images are performed with different JPEG quality factor (QF) values. The quality factor down to 5% is applied and watermark can be detected by the detector.
Cascading Attacks:
The watermarked images are also tested against cascading attacks. Firstly, the image is subjected to Weiner filter, then the images were compressed with different JPEG QF 75%,50%,25% etc, and finally noise with different power of 500,1000,50000,10000, and 15000 was added to the same corrupted image. The detector still can detect watermark after each set of attacks.
Geometric Attacks:
In order to show the robustness against geometric attacks, cropping are used. Cropping with different rates like 75%, 50%, 15% are applied. The watermark is robust to cropping attack as watermark is still detected after the said attack.
Watermark Lena image is tested against the resize attack. A 512 ×512 image is resized to ½ and ¾ of its original size and watermark detector response is well above the threshold .Which shows that our technique is robust against the resize attack.
Watermark is also tested against rotation attack of degrees +45 and -45. After performing rotation attack, the detector still detects the watermark.
Matlab functions of im2single, im2double and zeropading rescaling attacks are also performed on the watermarked images and our technique is robust to these attacks.
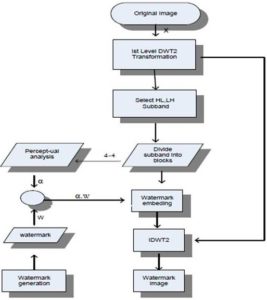
Several GP simulations are carried out to get the best expression, through which optimal strength watermark was embedded in the images.
Formula: ‘—(—(—(—(coef, 0.16554), sin(X1)), contrast), coef)’
Where contrast is the contrast sensitivity, coef is the DWT coefficient and X1 is the luminance value of a pixel in an image.
Experimental Results
The watermark embedding and watermark detection are performed on standard images as mentioned in section 4 above. The images are selected with different characteristic such as texture, flat, curves, contrast, smooth, light reflecting surfaces etc. They all are gray images of size 512×512. Fig.3 summarizes the measured values of PSNR, MSE and Structure Similarity Index Measure (SSIM) after attacks. PSNR and SSIM are the imperceptibility measures. The greater the value of PSNR, and the lesser the value of MSE, the better the imperceptibility of the watermarked image. Fig.3 also demonstrates the imperceptibility comparison of the proposed technique with Khan et al (2006), in terms of quality of watermarked image measured in PSNR, MSE, SSIM for different training images. The WPM represents Watson Perceptual Model and GPM is Genetic Perceptual Model proposed by Khan et al (2006).
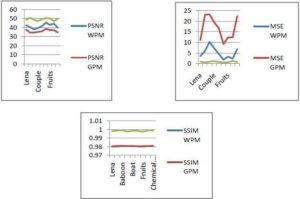
Fig.3. Imperceptibility Comparison of the Proposed Technique with Other Techniques
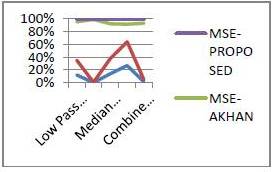
Fig.4 summarizes the average performance of different attacks on watermarked image and its comparison with other techniques. It is noticeable that the proposed technique outperforms the technique of Khan et al (2006). The improvement in terms of higher PSNR and SSIM values, and lower values for MSE.
Fig.4. Robust Comparison of After Attacks Average Values of the PSNR and MSE of Proposed Technique with Other Techniques