Introduction
In today’s world, information technology is indispensable for business. To ensure the proper functioning of information technology (IT) and information systems (IS), their continuous operation, and safety, it is very important to manage them properly in all areas that concern them. Therefore, in this article, we focus on the conceptual frameworks that have been selected to cover each important area of IT. Under the term conceptual frameworks, we understand frameworks like CoBIT and ITIL, international standards like ISO/IEC 20000, 27001, 22313, 22301 and PCI/DSS, policies, financial assessments and other methodologies.
To determine the current state of use of conceptual frameworks by companies, we conducted a preliminary survey on a sample of 75 companies. The survey aimed to find out the use of these frameworks in practice and identify survey weaknesses. The outputs identified by this survey will be used to design a larger survey with the aim to a conceptual IT service management model (ITSM) for small and medium-sized enterprises.
ITSM can be defined as a set of processes that works together on direct quality assurance of IT services, according to the service level agreed by the customer (Lubis, Annisyah and Winiyanti, 2020). ITSM philosophy is based on how customers perceive IT contribution to the business, in reducing cost as well as IT service provision (Hermanto and Kusnanto, 2017).
This scientific paper consists of several consecutive parts. The literature review provides an overview of the current state of conceptual frameworks in the field of IT management. The research objectives and methodology sections present the research aim, the research tools, and the data set format. The results and discussion consist of realized research outcomes and main findings.
Literature Review
In this chapter, we focus on a more detailed definition of selected conceptual frameworks used in the field of IT management. Best practices in enterprise IT management are very important as they support not only better process management in this area, but also the management of IT activities, which are also one of the decisive factors for the success of an organization (ITGI, 2008). These practices provide effective support for managers seeking to improve their business through better use of IT.
Within the realized survey, we have chosen conceptual frameworks, which cover the whole spectrum of areas that need to be ensured within the optimal operation of information technologies in the enterprise. A basic overview of these conceptual frameworks is presented in tab. 1.
Mentioned conceptual frameworks provide comprehensive coverage of IT areas in the enterprise. In addition to these conceptual frameworks, businesses can use also others, which are not captured in our overview. Alternatively, they can develop their own procedures and methods to cover IT-related areas.
Table 1: Conceptual frameworks overview
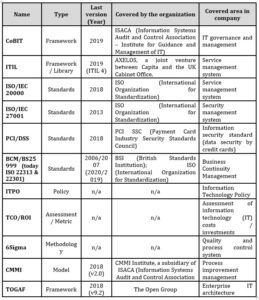
Source: Authors’ processing
CoBIT refers to Control Objectives for Information and Related Technologies. It is framework, which helps the senior executives to fill the gap in control requirements, technical issues, and business risks (Saeedinezhad and Naghsh, 2019). In addition, it supports the IT management by combining business goals with technology goals and processes (Vugec, Spremić and Bach, 2017). CoBIT provides clear guidelines for controlling IT management in companies with a measure of maturity at each level, this helps organizations to increase the value to be achieved by the use of IT (Aprilinda, Puspa, and Affandy 2019). CoBIT is improving/implementing governance and management of IT, IT/IS/information/cybersecurity, risk management, compliances, assurance, strategic alignment, etc., for enterprises (large, medium or small) (Rafeq, 2019). Thus, we can state that COBIT 5 is the framework for corporate IT governance, focusing on the description, set of processes, guidelines, objectives, best practice assessment and indicators to maximize IT utilization to achieve business goals. It is the only integrated framework for managing IT, promoting a holistic approach, and distinguishing IT governance from IT management activities.
Another examined conceptual framework is ITIL. The Information Technology Infrastructure Library (ITIL) is a set of detailed practices for IT service management that focuses on aligning IT services with the needs of business (Vicente, Gama, and Silva, 2013). ITIL defines a service as a means of delivering value to customers by facilitating outcomes customers want to achieve without the ownership of specific costs and risks. According to the authors Moscoso-Zea, Paredes-Gualtor, Luján-Mora (2019), ITIL can be considered as an iterative tool that focuses on the maturity process. The ITIL V3 Service Lifecycle is compound by five processes (all describe guidelines):
- Service strategy: development and implementation of service management.
- Service design: design appropriate and innovative IT services.
- Service transition: deliver services to meet current and future business requirements.
- Service operation: coordinate and carry out delivery and management process.
- Continual service improvement: maintain the value of customers through the continual evaluation and improvement of the business services.
The current available version of ITIL is ITIL V4, which was released in early 2019. This version is based on its predecessor ITIL V3. ITIL3 encompasses 26 processes divided around the service lifecycle. ITIL V4 replaced these processes by 34 practices. These practices cover almost all ITIL V3 processes and leave the organization more freedom by defining its own processes in these areas. The service lifecycle replaces ITIL V4 with service value chain with its six activities- plan, improve, engage, design and transition, obtain/build, deliver and support, which lead to the creation of products and services and in turn, value (Axelos, 2019). ITIL as a library of best practices in IT service management covering the entire IT service lifecycle. These practices are recommendations, so enterprises can use them as an inspiration to set up their own ITSM concept, or choose the ones they consider most appropriate. Due to the still large use of ITIL3 in companies, we present both versions here, and we did not distinguish between their versions in the survey.
ISO/IEC 20000 is an international standard in the field of IT service management. It specifies requirements for an organization to establish, implement, maintain and continually improve a service management system (SMS). ISO/IEC 20000 includes the planning, design, transition, delivery and improvement of services to meet the service requirements and deliver value similar to ITIL, but there are differences between them. ISO/IEC 20000 has a different purpose than the use of ITIL. According to Jasek, Kralik and Popelka (2014), the aim of ISO/IEC 20000 is to present clear objective requirements to verify that the set of best practices according to ITIL was applied. ISO / IEC 20000 enables an independent certification service management process.
Another international standard we are mentioning is ISO/IEC 27001. It assists organizations in developing and maintaining an information security management system (ISMS) on the organizational level (Disterer, 2013). The use of the ISO/IEC 27001 standard has seen an increasing trend due to massive digitization. Since firms increasingly store their information based on ICT and governments and suppliers, more and more require firms to ensure information security (Mirtsch, Kinne, and Blind, 2021).
PCI/DSS standards focus on the security area, even only on a smaller part of it (securing payments data). We chose this because of the significant use of online payments within eCommerce solutions and the need for companies to keep this transaction data safe, for which they can use this standard. The PCI DSS basically standardizes a set of practices and measurements to secure sensitive cardholder data. It guides merchants, service providers, and acquirers involved in dealing with payment card data and helps prevent the risk of credit card fraud. Moreover, it provides enhanced and consistent standards and practices to secure the payment card transaction data and hence provide a high degree of confidentiality and integrity to stakeholder information (Jing, L., et al., 2010).
Business continuity management (BCM) is essentially close to safety. It is described as a holistic management process that identifies potential threats to an organization and the impacts to business operations that those threats, if realized, might cause, and which provides a framework for building organizational resilience with the capability for an effective response that safeguards the interests of its key stakeholders, reputation, branch and value-creating activities (BS 25999-2, 2007). BS 25999 was created to set out a uniform benchmark in good practice, satisfying the needs of customers, clients, government, regulators and all other interested parties. BS 25999 has been accepted worldwide and has formed the basis of many other BCM standards, including the US ASIS/BSI BCM.01 standard adopted by ANSI. BS 25999 and other BCM standards from across the globe provided the source material for the creation of two new international standards: ISO 22301 (requirements) and ISO 22313 (guidance) (BSI, 2012).
The Information Technology Policy Office (ITPO) was included among the conceptual frameworks due to the representation of the formalization of rules in the field of IT applied in the company into comprehensive policies. ITPO handles IT policy development, dissemination, and education (Waliullah, Arafat and Daiyan, 2012).
Total Cost of Ownership (TCO) is a comprehensive assessment of information technology or other costs across enterprise boundaries over time. It includes hardware and software acquisition, management and support, communications, end-user expenses and the opportunity cost of downtime, training and other productivity losses (hidden costs) (Gartner, 2021). According to Botchkarev and Andru (2011), ROI is defined as a fraction, the numerator of which is “net gain” (return, profit, benefit) earned as a result of the project (activity, system operations), while the denominator is the “cost” (investment) spent to achieve the result. The purposes of ROI are: providing a rationale for future investments and acquisition decisions, evaluating existing systems and performance management of the business units and evaluation of the individual managers in decentralized companies. Together with TCO, these are used in enterprise as assessment tools of IT ownership. They cover not only the cost side but also the revenue side.
Six Sigma is a business methodology and practice driven by data and statistical analysis. It helps to minimize errors and maximize value from manufacturing to non-manufacturing segment (i.e., software and technology environments) (Wong and Yu, 2020). In the past two decades, the adoption and implementation of Six Sigma into IT-related project activities have drawn great attention from both the industry and academic sector. According to the survey result by Wong (2012).
The Capability Maturity Model Integration (CMMI) model is an integrated maturity model based on the maturity model (CMM) and built on TQM principles. By applying the IT service management model, it is possible to map the state of processes and process management as well as other related technological, knowledge and organizational elements. It defines several levels of process maturity – incomplete, initial, managed, defined, quantitatively managed, and optimizing (CMMI, 2019). Determining the process maturity is based on a comprehensive assessment of the process and its process management as a whole.
The Open Group Architecture Framework (TOGAF) is a framework of enterprise architecture creation processes. According to this framework, enterprise architecture consists of business architecture (business strategy, governance, organization and key business processes), data architecture (logical and physical data assets and data resources management), application architecture (applications and their relationships to the core business processes) and technology architectures (software and hardware components). We further analyzed the use of these conceptual frameworks using a quantitative survey.
Research objectives and methodology
In this scientific paper, we focus on the analysis of identified conceptual frameworks used in the field of IT management in organizations operating in the Slovak republic. The preliminary study aims to obtain a basic overview of the used conceptual frameworks to create an overview of the current situation in practice and to obtain data for creating a detailed concept of further large-scale research. The ambition of further research is to design an ITSM model for small and medium enterprises.
The analysis of the available theoretical literature was performed by searching for available sources in scientific databases, professional literature, and other sources on the Internet. Using the synthesis of the obtained data, we created the conceptual framework list shown in tab. 1.
The next step was to carry out a preliminary survey of the use of these conceptual frameworks. To obtain data, we used a questionnaire survey applied among companies in Slovakia. The survey has been conducted between companies in the Slovak republic. The aim of the preliminary research was 50 answers (actually obtained N=75). The collected sample also forms the limits of this preliminary analysis, as it partly affects the resulting data. Data were collected electronically during the year 2020 and subsequently evaluated using statistical software.
We intended to verify the choice of identified conceptual frameworks and to identify the types of conceptual frameworks used by micro, small and medium-sized enterprises. To categorize enterprises by size, we used the definition of European Commission (2012) for Small and medium-sized enterprises (SMEs), which we present in tab. 2. We have classified all companies with a higher number of employees or turnover among large companies.
Table 2: SMEs categorization
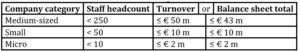
Source: European Commission (2012)
The research sample included 75 enterprises, with the large share companies operating in Europe (42,7%), worldwide (26,7), in Slovakia and Czech Republic (10,7%) and only in Slovakia (20%). In terms of sectoral coverage, the biggest shares had Industrial production (25,3%), Financial and insurance activities (16%), Information and communication (13,3%), Wholesale and retail; repair of motor vehicles and motorcycles (12%), Professional, scientific and technical activities (12%), Other activities (8%), other sectors had below 5% each (total 13,4%). From the point of view of the ownership structure, whether the owners of companies are from Slovakia or abroad, the biggest share had exclusive foreign owner (39%), the dominant foreign owner (21,6%), the exclusive home owner (23%), the dominant home owner (16,4%). The distribution of enterprises by size is displayed in tab. 3. The structure of the surveyed sample according to the IS/IT customer or the IS/IT contractor is the following: IS/IT customers (57,3%), suppliers of IS/IT products and services (42,7%).
Table 3: Distribution of enterprises by size categories (ESC)
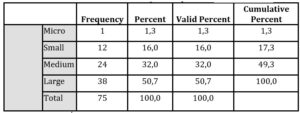
Source: Authors’ calculations
To analyze data, we used some statistical methods and data display methods. When verifying the dependence between variables, we used the statistical method Eta to measure the dependence between the nominal and interval variables. The data were tested at the level of significance a = 0.05.
Results And Discussion
In this section, we will take a closer look at the findings of the survey. Based on the obtained data, we aggregated the numbers of used conceptual frameworks and divided them by size categories of enterprises. The overview is displayed in tab. 4.
Table 4: Number of frameworks according to enterprise size categories
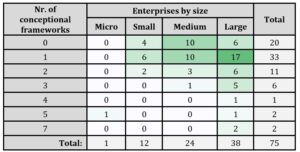
Source: Authors’ calculations
Based on the data, we can assume that these conceptual frameworks are almost entirely unused in micro-enterprises, which could be logically assumed because the implementation of the frameworks requires considerable human and financial resources, which is not inside the capabilities of micro-enterprises. However, the situation is changing for small and medium-sized enterprises, where these frameworks are beginning to be used in the range of one to two per enterprise. For large companies, the need for the presented frameworks is high, but there are still companies, which do not use any of the mentioned frameworks.
In the analysis of the dependence between the stated variables using the statistical method Eta, we measured the mean dependence (Eta = 0,438) for the dependent variable the number of conceptual frameworks, which confirms our assumptions of a direct dependence between the size of the company and the number of conceptual frameworks.
A similar dependence was demonstrated in the analysis of the relationship between the existence of an information strategy in the company and the number of conceptual frameworks. The measured dependence is of medium intensity (Eta = 0,385) by the dependent variable, the number of conceptual frameworks, and the independent existence of an information strategy. This dependence has a similar explanation as in the first case, that larger companies have enough resources to develop an information strategy (Eta = 0,406; medium dependency; dependent variable – the existence of an information strategy; independent variable – enterprise size category). The above findings confirm the assumption that larger firms need to use conceptual frameworks and formalise the direction of the business in the form of an information strategy.
Table 5: Use of conceptual frameworks
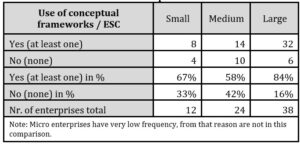
Source: Authors’ calculations
In tab. 5, we provide a percentage overview of enterprises that use at least one conceptual framework. In this area, we can conclude that, although with a greater degree of inaccuracy due to a small sample of enterprises in certain categories, there is a visible effort in enterprises to use practice-proven conceptual frameworks. In further research, we will also focus on the analysis of factors influencing the implementation and use of conceptual frameworks.
In the next section, we will focus on analyzing and evaluating the use of individual conceptual frameworks in enterprises broken down by their size categories. See tab. 6 for an overview. The table below shows the number of companies using the conceptual framework, while one company can use more than one conceptual framework.
We have made the following summaries from the performed analysis. It is evident that COBIT is mainly used by large enterprises. This framework focuses mainly on IT Governance. It links strategic management of the company with IT management, which is necessary to formalize especially in large and medium-sized enterprises. In smaller companies, this need is not so significant, which is mainly related to a less extensive organizational structure and fewer employees.
Table 6: Numbers of conceptional frameworks according to ESC
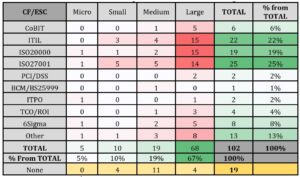
Source: Authors’ calculations
The ITIL framework and the international standard ISO/IEC 20000 both focus on the management of IT services. Based on the obtained results, we can conclude that this area is seen as important for a large part of businesses. The ISO/IEC 27001 standard deals with the area of IT security and is also quite often adopted by companies, which points to the perception of IT security as an important area for companies. Based on the previous information, we concluded that, in compiling a simple conceptual framework for SMEs, it will be necessary to prioritize mainly these two areas, such as IT service management and IT security. Other conceptual frameworks are used more or less sporadically and due to the small research sample, we will not make any assumptions from them.
In the previous analysis, we focused on identifying the relationship between the size of the company (determined by the categories micro, small, medium and large) and the number of conceptual frameworks used. We also identified which conceptual frameworks companies use according to their size in these categories.
In the following section, we will discuss in more detail the possible relationships between the number of employees in the company, the amount of turnover of the company, the geographical scope of the company, the structure of its owners to the number of conceptual frameworks used. The distribution of the number of enterprises in individual categories is presented in tab. 7.
Table 7: The distribution of the number of enterprises in individual categories
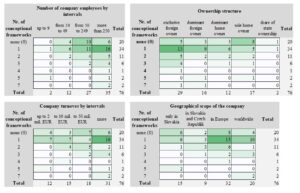
Source: Authors’ calculations
In the listed categories, we performed the measurement of the dependence using the statistical method Eta k dependent variable the number of conceptual frameworks. The results of measurements are presented in figure 1. According to the obtained values, we can state that the highest dependence is between the number of employees in the company and the number of conceptual frameworks. The intensity of this dependence can be assessed as a medium (Eta = 0,345) for the dependent variable the number of conceptual frameworks. The expected explanation is that the companies with a higher number of employees need to manage them effectively and therefore implement various conceptual frameworks. We also measured a similar dependence between companies divided into size categories (micro, small, medium and large), where companies were included in these categories based on an assessment of the number of employees and also the level of turnover. However, in the area of dependence between the turnover level and the number of used conceptual frameworks, we measured only a weak dependence (Eta = 0,182, for the dependent variable the number of conceptual frameworks). Therefore, we could assume that the primary category that determines the number of conceptual frameworks used is the size of the organization measured by the number of employees in the organization.
On the other hand, when analyzing the impact of the number of IT employees on the use of conceptual frameworks, there is no apparent relationship. Even the dependence measurement itself determined only a small dependence Eta = 0,249, dependent variable – number of conceptual frameworks, independent variable – how many full-time IT professionals are employed in your company. This means that the number of IT employees does not affect the use of the conceptual framework.
It is possible to identify from other results a weak dependency (Eta = 0,205, for the dependent variable the number of conceptual frameworks) between the owner structure and the number of conceptual frameworks used. Looking at the table, we can state on the basis of the calculated percentages when the company has exclusively a foreign owner, then it has implemented more conceptual frameworks and vice versa. In the case of an exclusive foreign owner, 82.8% of companies have implemented at least one conceptual framework, while in the case of an exclusively domestic owner it is only 52.9%.
The last category is the dependence between the geographical scope of the company and the number of implemented conceptual frameworks. This dependence is the weakest (Eta = 0.173, for the dependent variable the number of conceptual frameworks), but similarly, although not as significantly as by the structure of owners, we see a certain relationship between companies operating abroad (Europe and the world) and the number of implemented conceptual frameworks. Based on the above, we can say that abroad (Europe and the world – 76.9% have implemented at least one conceptual framework) companies have more common use of existing conceptual frameworks compared to the domestic environment, or in connection with the Czech Republic (SK + SK&CZ – 66.7% have implemented at least one conceptual framework), but the difference is not high at all and the dependence of these areas is weak.
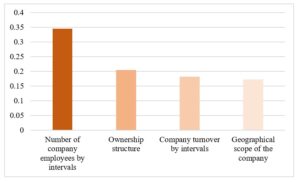
Fig 1. The size of the dependence between dependent variable nr. of conceptional frameworks and company categories
Source: Authors’ calculations
In our further analysis, we focused on the impact of criteria such as IT Contractor / Customer and number of IT employees on the number of conceptual frameworks. Outputs are presented in tab.
Table 8: How criteria IS/IT Contractor or Customer & number of IT employees influence the number of conceptual frameworks
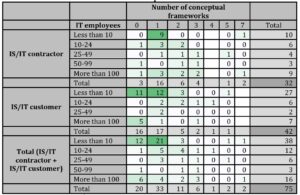
Source: Authors’ calculations
From the data given in tab. 8, it can be stated that the number of implemented conceptual frameworks is most influenced by whether it is an IT contractor or an IT customer, while most contractors have implemented at least one conceptual framework. The measured correlation is Eta = 0,306, dependent variable – number of conceptual frameworks, independent variable – IT Contractor or Customer. That correlation has a medium intensity, even though only from the lower side of the interval.
If IT staff does not influence the number of conceptual frameworks adopted by the organization, we analyzed whether the existence of an IS / IT department or manager has an impact. The results are shown in tab. 9.
Table 9: Existence of IS/IT department or manager and number of conc. Frameworks
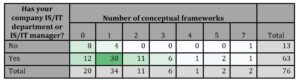
Source: Authors’ calculations
Based on the obtained data, we can state that an organization that has an IS / IT department or manager has implemented more conceptual frameworks than one that does not. We used a symmetric measurement to determine the dependence Cramer’s V = 0,425; p = 0,033. Based on the above measurements, we can state that the dependence is of medium intensity.
In the next analysis, we focus on the level of management of the processes that take place in the company in relation to the perception of IT in the company and its involvement in the processes. We verified the assumption of whether there is a link between the level of definition of processes in the company in relation to IT and the use or non-use of any conceptual framework. We assume that there will be dependence between these areas, as most conceptual frameworks are implemented in business processes.
To determine the level of management of the processes taking place in the company in relation to the IT area, we asked respondents to determine their level of agreement with the above statements in relation to the situation in their organization on a scale from 0 to 100, where zero meant complete disagreement and 100 meant full agreement:
- Business processes are defined and described.
- The ownership of the process is clearly defined and described.
- There is a defined link between IT and business processes.
- IT is more perceived as a business support service than just a technology solution.
The distribution of respondents’ answers within the above scale for all four statements, expressed as a percentage, as shown in the following graphs.
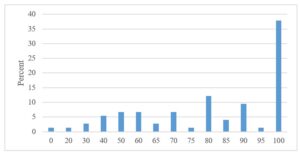
Fig 2. Business processes are defined and described
Source: Authors’ calculations
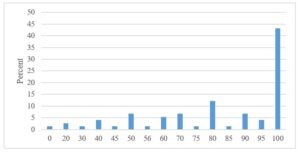
Fig 3. The ownership of the process is clearly defined and described
Source: Authors’ calculations
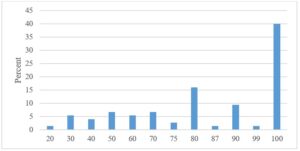
Fig 4. There is a defined link between IT and business processes
Source: Authors’ calculations
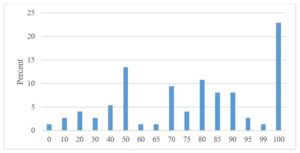
Fig 5. IT is more perceived as a business support service than just a technology solution.
Source: Authors’ calculations
From the above graphs, we see that the organizations in the area of the process definition (Fig 2. and 3.) evaluate themselves relatively positively, as the largest percentage of responses was by 100, which means full agreement with the statement. A similar situation is also by the connection between IT and business processes (Fig 4.). A slightly more even distribution of responses across the scale was only in the perception of IT in the organization. Not so many organizations understand IT as a business support service, and there are still many who perceive it only from a technological point of view (Fig 5.).
We used primarily to measure the dependencies between the use or non-use of at least one conceptual framework and the degree of consent of respondents to the above claims; the statistical methods Eta and Cramer V. Calculated results are presented in tab. 10.
Table 10: Results of statistical measurement of dependencies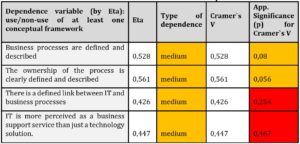
Source: Authors’ calculations
When evaluating relationships using the Eta statistical method, we can state that there is a medium-strong relationship between all claims and the use or non-use of at least one conceptual framework. This confirms our assumption that the better the processes in companies are formalized and defined, the more companies understand the need to formalize IS/IT management by using some of the conceptual frameworks used in this area. The significance (p) for the Cramer V statistical method is close to an acceptable level of 0,05.
If we also focus on the relationship between IT and business processes, or on the understanding of IT as a business support service, here the relationship expressed using the statistical method Eta is slightly weaker, but we can still evaluate it as moderate intensity. However, the significance (p) for the Cramer V statistical method is high above the acceptable level of 0,05.
Conclusion
Conceptual IT frameworks help companies manage their IT better and more securely. Therefore, it is important that as many companies as possible implement these conceptual frameworks. At the beginning of this article, we provide an overview of the conceptual frameworks covering most IT areas in the enterprise. Furthermore, we analyze a questionnaire survey, which gave us a better perception of the use of these conceptual frameworks in companies operating in the Slovak Republic and how is their use influenced by the factors characterizing formalization in the IT area through existing IT departments, the position of IT manager or the number of IT employees, the existence of an IT strategy and also the size of the company. We also looked at the possible relationships between the number of employees in the company, the amount of turnover of the company, the geographical scope of the company, the structure of its owners to the number of conceptual frameworks used and on the level of management of the processes taking place in the company in relation to the IT area. These findings, together with other facts, will be examined in more detail in further research.
In further research, we will focus on creating a conceptual framework for SMEs, which will be simple and understandable to implement, so companies do not have to spend a lot of effort and resources on its implementation and operation. Before we start to design it, we will take a closer look at the reasons why companies did not decide to implement any of these mentioned frameworks, we will focus on these obstacles and help eliminate them.
The performed analysis helped us to set the further direction of research, although due to the smaller size of the examined sample, it is necessary to assess some assumptions with a greater degree of variability.
Acknowledgments
The paper was elaborated within VEGA No. 1/0388/20 IT Management in Enterprises in Slovakia: International Standards and Norms Versus Individual Business Processes – proportion 100.
References
- Aprilinda, Y., Puspa, A. K. and Affandy, F. N. (2019), ‘The Use of ISO and COBIT for IT Governance Audit’ Proceedings of The 1st International Conference on Engineering and Applied Science, August 2019, Madiun, East java, Indonesia, 1381.
- (2019). ITIL® Foundation ITIL 4 Edition, The Stationery Office, Norwich, ISBN 9780113316076
- Botchkarev, A. and Andru, P. (2011), ‘A Return on Investment as a Metric for Evaluating Information Systems: Taxonomy and Application,’ Interdisciplinary Journal of Information, Knowledge, and Management, 6, 243-269.
- BS 25999-2, 2007, Business Continuity Management, Part 2: Specification, British Standards Institution
- CMMI, CMMI Levels of Capability and Performance. [online], [Retrieved. June 06, 2019], https://cmmiinstitute.com/learning/appraisals/levels
- CoBit, Information Systems Audit and Control Association (ISACA). [online], [Retrieved February 09, 2021], https://www.isaca.org/resources/cobit
- Disterer, G. (2013), ‘ISO/IEC 27000, 27001 and 27002 for information security management,’ Inf. Secur, 4(2), 92–100.
- Hermanto, A. and Kusnanto, G. (2017). ‘Evaluation of the information technology system services for medium higher education based on ITIL (A case study of polytechnic XYZ)’ Proceedings of 4th International Conference on Computer Applications and Information Processing Technology (CAIPT), August 2017, Kuta Bali, Indonesia, 1-8.
- ISO 22301:2019, International Organization for Standardization (ISO). [online], [Retrieved February 09, 2021], https://www.iso.org/standard/75106.html
- ISO 22313:2020, International Organization for Standardization (ISO). [online], [Retrieved February 09, 2021], https://www.iso.org/standard/75107.html
- ISO/IEC 20000-1:2018, International Organization for Standardization (ISO). [online], [Retrieved February 09, 2021], https://www.iso.org/standard/70636.html
- ISO/IEC 27001:2013, International Organization for Standardization (ISO). [online], [Retrieved February 09, 2021], https://www.iso.org/standard/54534.html
- IT Governance Institute ITGI 2008. Enterprise value: Governance of IT investments. Getting started with value management. [online], [Retrieved. June 06, 2013], http://www.itgi.org
- Jasek, R., Kralik, L. and Popelka, M. (2014), ‘ITIL (R) and Information Security’ Proceedings of International Conference on Numerical Analysis and Applied Mathematics (ICNAAM). September 2014, Rhodes, Greece, 1648.
- Jing, L., et al. (2010), ‘A Survey of Payment Card Industry Data Security Standard,’ IEEE COMMUNICATIONS SURVEYS AND TUTORIALS, 12 (3), 287-303.
- Lainhart, J., Conboy, M. and Saull, R. (2019). COBIT 2019 Framework: Governance and Management Objectives, ISACA, ISBN: 978-1-60420-764-4, 4-7
- Lubis, M., Annisyah, R. C. and Winiyanti, L. L. (2020), ‘ITSM Analysis using ITIL V3 in Service Operation in PT.Inovasi Tjaraka Buana’ Proceedings of IOP Conf. Series: Materials Science and Engineering, March 2020, Batu, Malang – East Java, Indonesia, 847.
- Mirtsch, M., Kinne, J. and Blind, K. (2021) ‘Exploring the Adoption of the International Information Security Management System Standard ISO/IEC 27001: A Web Mining-Based Analysis,’ IEEE TRANSACTIONS ON ENGINEERING MANAGEMENT, 68(1), 87-100.
- Moscoso-Zea, O., Paredes-Gualtor, J. and Luján-Mora, S. (2019). ‘Enterprise Architecture, an enabler of change and knowledge management,’ Enfoque UTE, 10(1), 247-257.
- British Standards Institution (BSI), Moving from BS 25999-2 to ISO 22301. [online], [Retrieved February 09, 2021], https://www.bsigroup.com/Documents/iso-22301/resources/BSI-BS25999-to-ISO22301-Transition-UK-EN.pdf
- Office of Government Commerce. (2007) The Official Introduction to the ITIL Service Lifecycle, The Stationery Office, Norwich, ISBN 9780113310616
- PCI SECURITY, Security Standards Council (PCI). [online], [Retrieved February 09, 2021], https://www.pcisecuritystandards.org/pci_security/
- Rafeq, A., (2019), COBIT Design Factors: A Dynamic Approach to Tailoring Governance in the Era of Digital Disruption. [online], [Retrieved February 09, 2021], http://www.isaca.org/COBIT/focus/Pages/cobit-design-factors.aspx
- Saeedinezhad, S. and Naghsh, A. (2019). ‘Management of IT Services in the Field of Pre-Hospital Emergency Management with the Combined Approach of COBIT Maturity Model and ITIL Framework: A Conceptual Model,’ Journal of Health Management and Informatics, 6(3), 85–95.
- SME definition [online]. European Commision. [Retrieved February 09, 2021], https://ec.europa.eu/growth/smes/sme-definition_en
- Total Cost of Ownership (TCO) [online]. [Retrieved February 10, 2021], https://www.gartner.com/en/information-technology/glossary/total-cost-of-ownership-tco
- Vicente, M., Gama, N., and Silva, M. M. (2013), ‘The Value of ITIL in Enterprise Architecture,’ Proceedings of 17th IEEE International Enterprise Distributed Object Computing Conference, September 2013. Vancouver, BC, Canada, 147-152.
- Vugec, D. S., Spremić, M. and Bach, M. P. (2017), ‘It Governance Adoption in Banking and Insurance Sector: Longitudinal Case Study of COBIT Use,’ International Journal for Quality Research, 11(3), 691-716.
- Waliullah, M., Arafat, J. and Daiyan, G.M. (2012), ‘Information Technology Security, Strategies and Practices in Higher Education: A Literature Review,’ JOURNAL OF COMPUTING, 4 (7), 138-144.
- Advisera, What is BS 25999? [online], [Retrieved February 09, 2021], https://advisera.com/27001academy/what-is-bs-25999/
- Axelos, What is ITIL. [online], [Retrieved February 09, 2021], https://www.axelos.com/best-practice-solutions/itil/what-is-itil
- Wong, W. , Tshai, K. , Lee, C. (2012), ‘The Evolution of Quality Improvement Methodology in Malaysia-s IT Industry: The Past, Current and Future’, World Academy of Science, Engineering and Technology, Open Science Index 72, International Journal of Industrial and Manufacturing Engineering, 6(12), 2691 – 2700.
- Wong, W.Y. and Yu, S.W. (2020), ‘Six Sigma Practices and Implementation for Information Technology Project: Key Questions to Guide Better Understanding and Decision Making’ Proceedings of 16th IEEE International Colloquium on Signal Processing & its Applications (CSPA 2020), Langkawi, Malaysia, 318-323.


















